hashcat - advanced password recovery
World's fastest and most advanced password recovery utility

Stats
Alexa Rank: 91545
Popular in Country: United States
Country Alexa Rank: 83162
language:
Response Time: 0.053623
SSL: Enable
Status: up
Code To Txt Ratio
Word Count 1010
Links
ratio 31.945779657758
SSL Details
SSL Issuer:
Issuer: Sectigo RSA Domain Validation Secure Server CA
Valid From: 2021-11-19 00:00:00
Expiration Date: 2022-12-20 23:59:59
SSL Organization:
Signature 4cf213d02d543ff5f437b28ac8394bfe43ca9d1d
Algorithm: RSA-SHA256
Found 71 Top Alternative to Hashcat.net

 Onlinehashcrack.com
Onlinehashcrack.com
Online Password Hash Crack - MD5 NTLM Wordpress Joomla WPA PMKID, Office, iTunes, Archive, ..
OnlineHashCrack is a powerful hash cracking and recovery online service for MD5 NTLM Wordpress Joomla SHA1 MySQL OSX WPA, PMKID, Office Docs, Archives, PDF, iTunes and more!
 Crackstation.net
Crackstation.net
CrackStation - Online Password Hash Cracking - MD5, SHA1, Linux, Rainbow Tables, etc.
Crackstation is the most effective hash cracking service. We crack: MD5, SHA1, SHA2, WPA, and much more...

 Miloserdov.org
Miloserdov.org
Ethical hacking and penetration testing - InfoSec, IT, Kali Linux, BlackArch
The complete guide to Wine: from installation to advanced usage Table of contents 1. Why Wine 2. Features and limitations of Wine 3. 64-bit or 32-bit Wine? 4. How to install Wine 4.1 Installing Wine on Debian, Kali Linux, Linux Mint, Ubuntu, and their derivatives 4.2 Installing Wine on Arch Linux 5. How...

 Openwall.com
Openwall.com
Openwall - bringing security into open computing environments
Information Security software for open computing environments, related publications, and professional services

 Tunnelsup.com
Tunnelsup.com
TunnelsUp - Tools and Information for Network Engineers
Tools, calculator, and helpful information for network engineering, web developers, and IT professionals.

 Wordpress.com
Wordpress.com
WordPress.com: Fast, Secure Managed WordPress Hosting
Create a free website or build a blog with ease on WordPress.com. Dozens of free, customizable, mobile-ready designs and themes. Free hosting and support.

 Aircrack-ng.org
Aircrack-ng.org
Aircrack-ng
Fresh news Aircrack-ng 1.7 10 May 22 After more than 2 years, we are making a release with a decently large amount of fixes, improvements, and additions. We also broke the 4000 commits barrier, and this release has more than 400 commits. Read more in our detailed blog post. PackageCloud.io...


 Md5decrypt.net
Md5decrypt.net
Md5 Decryption & Encryption Gratuite - Plus de 15.000.000.000 hashs
Decryption Md5 : Le Md5 (Message Digest 5) est une fonction cryptographique qui permet de "hasher" (encrypter) une séquence numérique en un hash md5 de 128 bits, soit 32 caractères, et ce peu importe la longueur de la séquence originale. Ce système cryptographique est irréversible, il n'est pas possible d'obtenir...
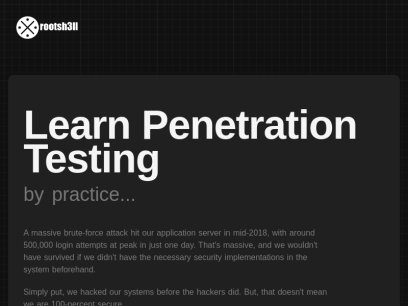
 Rootsh3ll.com
Rootsh3ll.com
welcome to rootsh3ll
Learn Penetration Testing by practice... A massive brute-force attack hit our application server in mid-2018, with around 500,000 login attempts at peak in just one day. That's massive, and we wouldn't have survived if we didn't have the necessary security implementations in the system beforehand. Simply put, we hacked our...

 Openwall.info
Openwall.info
Welcome to the Openwall Community Wiki! [Openwall Community Wiki]
Table of Contents Welcome to the Openwall Community Wiki! Software project specific resources Other projects Other resources External links Contact information Welcome to the Openwall Community Wiki! The idea is to have a DokuWiki namespace for each of our major projects, maybe resembling the directory structure of the main Openwall...
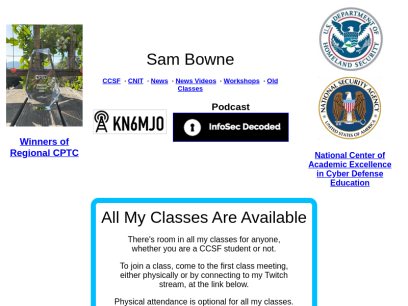
 Samsclass.info
Samsclass.info
samsclass.info: Sam Bowne Class Information
Pacific Hackers IhackNFT - Cryptocurrency CTF Fri, July 15, 2022, 9:00 AM - 5:00 PM PDT Hacker Dojo 855 Maude Ave · Mountain View, CA HOPE 2022 July 22-24, 2022 New York City Approved Workshops Violent Python 3 · Friday 22-July-2022, 12:00-15:00 · Workshop B Threat Hunting with Splunk ·...

 Zsecurity.org
Zsecurity.org
zSecurity – Ethical Hacking Courses, Tutorials, News, Products and more!
Hacking Masterclass by Zaid > Zaid’s NEWEST course. > Exclusive to zSecurity. > Enrol now and get 30% off. More information 745200 Students 1013150 Followers 219 Countries Latest Posts In Hacking & Security Capstone Challenge | Linux Privilege Escalation Linux Privilege Escalation: NFS || Episode 9 DNS Spoofing Basics with...
 Didierstevens.com
Didierstevens.com
Didier Stevens
-----BEGIN PGP PUBLIC KEY BLOCK----- Version: GnuPG v1.4.7 (MingW32) mQGiBEcg+PERBAC7Zex85WF3yfmGOfGjAMLsNx6y39rrmUjtNeGdHaFOS+RO2KQ9 19sXx5V42BVtsDae5qGFkAfdYi9uWiTiPHI4C3JXSnsVx1IHd4/Hr4vC/rncSwe/ emajuorUJwAB3FmWQm2lzSuS6FJNzpARGMH4X15O+dFy0pr0nJ79IFPO8wCghM5S yA8vcSvCDJ8bsKHruIpyN6MD/0GMNI3wK3Pb5OVJFDxVWQLrMaA8gdQBTiZ42aW+ 2rsyr1d61e94Nvurs0FwohzllfPyjX+NuiWcjlho2jnpkUO/iC/HcNzCAi3qN2Vv q6EfL8r7XVy/lG+OGhvYSnQU2GZjJyIltYjyKyhHD5P2GlBu9BSqN06bFgOdXcmB Bgb4A/9BqxOx8a+X3GiV1H+dnNfL7jS2CoH43Z3aXYCWgqMxEuvXvIrIPa6XAYNo /F5UGkONknBjxC/Pr9w/jORC8oW0AYZJlHmpTQOHedgsrCBPXmyYSu/pafS6O2V9 w5BGLpkmTQAX/Hr/DuGD0JGqVcOvGhVAgcrdBxDfEMNti+Lbw7QpRGlkaWVyIFN0 ZXZlbnMgPGRpZGllci5zdGV2ZW5zQGdtYWlsLmNvbT6IYAQTEQIAIAUCRyD48QIb AwYLCQgHAwIEFQIIAwQWAgMBAh4BAheAAAoJEHdz1uvbYxaW5iwAnRJp2jEfQ6h7 cvv4VT86VG6QzBzzAJ9l1FLWhOHDofRUAhZdYSLZjnURSbkCDQRHIPjxEAgAt21C uJWdsVbhnOOO/bfMuQOUrceh0DUDuO76QWrQSxz/vFSrVxBtSKct9GTICEk+3GXQ I1pmuxkAYcr3J1G36bKoPnMyX7x/+tJC+WkoroKzTVMlahdFjmI04Tc8iBYTwROn 8i6J5l9hoaNKLKfdV6Xmw0Y7A9w9wVRo09NkJiSzff3iQbis0mrh/jxup1coa4L+ 4FBjIHztt+7LXfwqKqBM1OnXvLPlSTJT4/KjRnCdNDy+zxz6g6Yzy4NNTcP0+EFr CijuE7/jLZho6P79Qt2nfe2O9BTQW6jIFaF2guvGMsEqgX9MtWxnd+P7KSz+1CtL sYkfiEdF8qp8ubHiswADBQf/XuRea1pMXKUs3f//Y7GRWtm2s9jPY5uSYqY7XaOm lsEflToedo8KxfymgA3axyI2QwxTEBnanPJQdPPd/vBSBCKmp5ihsFcKO30AKtbC J5SFRzTJmjwtaSRjI4CMZbIJCjb7uCSzF6ylEGIBypt+MbBXEhmGsv886Sm5PpR/ vXfZdtzFxMILJ8wgxSh5wtQ+rZHZUsPRszb45fUuaSPquStpndqp/Stx14s1LfGg Inpxn3eh+sz6iksaIb9mDZ5jcuRTx9rH43TkZRpdvk3WIHBo/6YFdOZUEhzKLYnO Fmjssq5wXIt2inj+C6H9kgLOYhb+bj8+GbdNhQT5oXH4EIhJBBgRAgAJBQJHIPjx AhsMAAoJEHdz1uvbYxaWAWoAoIH4MxPReBq32E2gmqrzOXXcL6BkAJ9L6FXNh9pH x7z8V6php7uMJQX6UA== =8AJk -----END PGP PUBLIC KEY BLOCK-----

 Portswigger.net
Portswigger.net
Web Application Security, Testing, & Scanning - PortSwigger
PortSwigger offers tools for web application security, testing, & scanning. Choose from a range of security tools, & identify the very latest vulnerabilities.
 Cvedetails.com
Cvedetails.com
CVE security vulnerability database. Security vulnerabilities, exploits, references and more
CVEdetails.com is a free CVE security vulnerability database/information source. You can view CVE vulnerability details, exploits, references, metasploit modules, full list of vulnerable products and cvss score reports and vulnerability trends over time

 Notsosecure.com
Notsosecure.com
NotSoSecure | Part of Claranet Cyber Security
NotSoSecure is one of the largest training providers at Black Hat conferences and trains hundreds of individuals throughout the year. Our trainers are also pen testers and we use a research led approach to ensure our training and testing is always of the highest quality.
 Nmap.org
Nmap.org
Nmap: the Network Mapper - Free Security Scanner
Nmap Free Security Scanner, Port Scanner, & Network Exploration Tool. Download open source software for Linux, Windows, UNIX, FreeBSD, etc.

 Acunetix.com
Acunetix.com
Acunetix | Web Application Security Scanner
Acunetix is an end-to-end web security scanner that offers a 360 view of an organization’s security. Allowing you to take control of the security of all you web applications, web services, and APIs to ensure long-term protection. Acunetix’s scanning engine is globally known and trusted for its unbeatable speed and precision.

 Rapid7.com
Rapid7.com
Cybersecurity & Compliance Solutions & Services | Rapid7
Supercharge your security impact with Rapid7, delivering shared visibility, analytics, and automation to unite security, IT, and DevOps teams.

 Kali.org
Kali.org
Kali Linux | Penetration Testing and Ethical Hacking Linux Distribution
Home of Kali Linux, an Advanced Penetration Testing Linux distribution used for Penetration Testing, Ethical Hacking and network security assessments.
 Xiaopan.co
Xiaopan.co
Main Navigation Menu Forums Xiaopan OS PRO XiaopanB Project Downloads Download Xiaopan OS Xiaopan OS Changelog Best Tiny Core Linux Apps How to Install Run in Virtual Machine Run From CD or DVD Run From USB Useful Linux Commands Modifying Xiaopan OS Change Language Wiki Help Xiaopan OS Xiaopan OS...
 Blackmoreops.com
Blackmoreops.com
Linux, InfoSec, Hacking - blackMORE Ops
blackMORE Ops is the leading source for Kali Linux, InfoSec, Hacking, Network and Cyber Security, How to, Guides and Tutorials with technical details.
 Passcape.com
Passcape.com
Password Recovery Software
Password Recovery Software to help you recover lost and forgotten passwords for Windows, Internet Explorer, Opera, Firefox, Outlook, IncrediMail etc. As well as DSL, dialup, vpn, wireless, LAN, and other network passwords.
 Hak5.org
Hak5.org
Hacking Tools & Media | Hak5 Official Site
Hak5 — industry leading hacker tools & award winning hacking shows for red teams, pentesters, cyber security students and IT professionals. Creators of the WiFi Pineapple, USB Rubber Ducky & more. Home to an inclusive information security community. Established in 2005.

 Scottlinux.com
Scottlinux.com
The scottlinux.com blog has become legacy and quite out of date. Look for the next thing cool thing here in the future. As always, rock on!

 Crark.net
Crark.net
cRARk - freeware RAR password recovery (Win, Linux, Mac, GPU)
Customer's FAQ 0. What is the password for the achive? There is no password to the crark's executables and configuration files. 1. I don't understand how to run your software. cRARk is command-line tool and the password recovery is controlled by password.def text file. If you are not aware with...
 Cmd5.org
Cmd5.org
Cmd5 - MD5 Online ,MD5 Decryption, MD5 Hash Decoder
This site provides online MD5 / sha1/ mysql / sha256 encryption and decryption services. We have a super huge database with more than 90T data records. Most are free, and a small amount is charged. This site can also decrypt types with salt in real time. This site was created...
 Project-rainbowcrack.com
Project-rainbowcrack.com
RainbowCrack - Crack Hashes with Rainbow Tables
RainbowCrack Introduction RainbowCrack is a general propose implementation of Philippe Oechslin's faster time-memory trade-off technique. It crack hashes with rainbow tables. Features Rainbow table generation, sort, merge, conversion and lookup Rainbow table of LM, NTLM, MD5, SHA1, SHA256 and customizable hash algorithms Rainbow table of customizable charset GPU acceleration with...

 Hackware.ru
Hackware.ru
HackWare.ru - Этичный хакинг и тестирование на проникновение, информационная безопасность
Вышла Kali Linux 2022.3: добавлена тестовая лаборатория и новые инструменты Разработчики Kali Linux выпустили новый релиз популярного дистрибутива для тестирования на проникновение. Пресс-релиз получился довольно объёмным из-за разносторонности данного дистрибутива и активности сообщества. С полным списком новостей вы можете ознакомиться по ссылке: Kali Linux 2022.3 Release (Discord & Test Lab):...

 Passwordrecovery.io
Passwordrecovery.io
Recovery of Password from Office documents (XLSX / DOCX), ZIP files and Hashes (Cisco, SHA1, MD5)
Online service to recovery lost passwords from office documents (doc, xls) and zip files. Also, search password hashes including md5, sha1 and sha256.
 Kalitut.com
Kalitut.com
KaliTut Linux and pentesting blog - KaliTut
Windows PowerShell tutorial for beginners Detailed PowerShell tutorial for beginners! ✓ Create and run PowerShell script, practice-oriented knowledge about PowerShell. Learn to Hack Steps from Beginner to Hacker Learn to hack , Beginner's Guide - with some many Tutorials on how to Hack Computers with Kali Install Linux PowerShell Tutorial...

 Cyberpratibha.com
Cyberpratibha.com
Cyber Pratibha | Enhance Cyber Skills
One Step Towards, Secure Cyber Word It's your turn to help to secure cyber space by enhancing your technical skills including Expertise in Linux, Wireless Security, Advanced in Kali Linux, Ethical Hacking and more Start Your Journy Work as volunteer Online Classes One to one, One to many classes make you | Cyber Pratibha

 Kali.tools
Kali.tools
Инструменты Kali Linux - Список инструментов для тестирования на проникновение и их описание
Сбор информации acccheck ace-voip Amap AQUATONE arp-scan Automater badKarma bing-ip2hosts braa Bro Bypass firewalls by abusing DNS history CaseFile CATPHISH CDPSnarf cisco-torch CloudFail Cookie Cadger copy-router-config DMitry dnmap dnsenum dnsmap DNSRecon dnstracer dnstwist dnswalk DotDotPwn Dublin Traceroute enum4linux enumIAX exploitdb EyeWitness Faraday FinalRecon Fierce Firewalk flashlight fragroute fragrouter Ghost Phisher...

 Asecuritysite.com
Asecuritysite.com
Security and So Many Things
Cipher test On-line Cipher test Printed Cipher Test Fun Tests Quick Jump (Cryptography) AES Blockchain/Cryptocurrency Ciphers Codes Cipher Cracking Crypto Pairing Curve 25519 Digital Cert and Trust Discrete Logs (solve) EdDSA, Ed25519 and Ed448 ElGamal Elliptic Curve ECDH ECDSA ECC Encryption (ECIES) Ethereum Factorization Format Preserving Enc Galois fields Hashing...
 Securityonline.info
Securityonline.info
Penetration Testing • Information Security
Securityonline is a huge security community. It is committed to the sharing of high-quality technical articles and safety reports, focusing on high-quality security and security incidents in the industry.
 Hashc.co.uk
Hashc.co.uk
HashRecovery - Recover your hashes
HashRecovery is a website that offers hash and password recovery services, it supports many hash algorithms including MD5, SHA1, bCrypt and much more...
 Darknet.org.uk
Darknet.org.uk
Darknet - Hacking Tools, Hacker News & Cyber Security
Darknet is your best source for the latest hacking tools, hacker news, cyber security best practices, ethical hacking & pen-testing.
 Adaywithtape.blogspot.com
Adaywithtape.blogspot.com
A day with Tape
1) probemon.sh The main script to monitor for WiFi probes, write backup files after reaching a certain size and logging restarts of the script. #!/usr/bin/bash DIR="/root/probemon/" # Directory for the working file and logs PROBELOG=probemon.txt # Working...
 Learntocodetogether.com
Learntocodetogether.com
Learn To Code Together | Learn wisely, be productive
Essential skills and comprehensive tutorials about computer science and the most prevalent technologies including JavaScript, Python, Java and more. Let's learn to code together!
 Thireus.com
Thireus.com
https://blog.thireus.com
 Kennyvn.com
Kennyvn.com
Kali Linux Tutorials - Kennyvn
A blog dedicated to sharing actionable Kali Linux tutorials, guides, cheatsheets, and tips and tricks.

 Darkmoreops.com
Darkmoreops.com
darkMORE Ops – More on the darker side ….
Recent Posts Handy MySQL Commands December 19, 2015 MITM – Man in the Middle Attack using Kali Linux November 16, 2015 DoS website with GoldenEye – Layer 7 DoS tool with KeepAlive NoCache November 22, 2014 Hack website password using WireShark November 11, 2014 Attack a website using slowhttptest from...
 Adeptus-mechanicus.com
Adeptus-mechanicus.com
Main
"Turning and turning in the widening gyre The falcon cannot hear the falconer; Things fall apart; the centre cannot hold; Mere anarchy is loosed upon the world, The blood-dimmed tide is loosed, and everywhere The ceremony of innocence is drowned; The best lack all conviction, while the worst Are full...

 Trustedsec.com
Trustedsec.com
TrustedSec | Cybersecurity
Cybersecurity consultants with expertise in penetration testing, social engineering and enterprise risk management - Learn how TrustedSec can help protect your company.
 N0where.net
N0where.net
CyberPunk Network
Welcome to CyberPunk PLTG Trix. No ELSUR. No ELINT. No censorship. No Ads. No data mining. No tracking. No Spyware.

 Korelogic.com
Korelogic.com
KoreLogic - Home
KoreLogic provides highly skilled cyber security services to Fortune 100 companies and the U.S. Government.
 Hashes.com
Hashes.com
Decrypt MD5, SHA1, MySQL, NTLM, SHA256, SHA512, Wordpress, Bcrypt hashes for free online
Decrypt and crack your MD5, SHA1, SHA256, MySQL, and NTLM hashes for free online. We also support Bcrypt, SHA512, Wordpress and many more.
Technologies Used by hashcat.net
Dns Records of hashcat.net
A Record: 151.80.143.33AAAA Record: 2001:41d0:302:2100::8aca
CNAME Record:
NS Record: ns04.domaincontrol.com ns03.domaincontrol.com
SOA Record: dns.jomax.net
MX Record: aspmx.l.google.com alt1.aspmx.l.google.com aspmx3.googlemail.com alt2.aspmx.l.google.com aspmx2.googlemail.com
SRV Record:
TXT Record: v=spf1 ip4:151.80.143.33 ip4:5.9.38.135 ip6:2001:41d0:302:2100::8aca include:_spf.google.com ~all
DNSKEY Record:
CAA Record: mailto:[email protected] letsencrypt.org sectigo.com
Whois Detail of hashcat.net
Domain Name: HASHCAT.NETRegistry Domain ID: 1580164009_DOMAIN_NET-VRSN
Registrar WHOIS Server: whois.godaddy.com
Registrar URL: https://www.godaddy.com
Updated Date: 2020-12-08T06:46:54Z
Creation Date: 2009-12-28T17:06:42Z
Registrar Registration Expiration Date: 2022-12-28T17:06:42Z
Registrar: GoDaddy.com, LLC
Registrar IANA ID: 146
Registrar Abuse Contact Email: [email protected]
Registrar Abuse Contact Phone: +1.4806242505
Domain Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited
Domain Status: clientUpdateProhibited https://icann.org/epp#clientUpdateProhibited
Domain Status: clientRenewProhibited https://icann.org/epp#clientRenewProhibited
Domain Status: clientDeleteProhibited https://icann.org/epp#clientDeleteProhibited
Registry Registrant ID: Not Available From Registry
Registrant Name: Registration Private
Registrant Organization: Domains By Proxy, LLC
Registrant Street: DomainsByProxy.com
Registrant Street: 2155 E Warner Rd
Registrant City: Tempe
Registrant State/Province: Arizona
Registrant Postal Code: 85284
Registrant Country: US
Registrant Phone: +1.4806242599
Registrant Phone Ext:
Registrant Fax: +1.4806242598
Registrant Fax Ext:
Registrant Email: Select Contact Domain Holder link at https://www.godaddy.com/whois/results.aspx?domain=HASHCAT.NET
Registry Admin ID: Not Available From Registry
Admin Name: Registration Private
Admin Organization: Domains By Proxy, LLC
Admin Street: DomainsByProxy.com
Admin Street: 2155 E Warner Rd
Admin City: Tempe
Admin State/Province: Arizona
Admin Postal Code: 85284
Admin Country: US
Admin Phone: +1.4806242599
Admin Phone Ext:
Admin Fax: +1.4806242598
Admin Fax Ext:
Admin Email: Select Contact Domain Holder link at https://www.godaddy.com/whois/results.aspx?domain=HASHCAT.NET
Registry Tech ID: Not Available From Registry
Tech Name: Registration Private
Tech Organization: Domains By Proxy, LLC
Tech Street: DomainsByProxy.com
Tech Street: 2155 E Warner Rd
Tech City: Tempe
Tech State/Province: Arizona
Tech Postal Code: 85284
Tech Country: US
Tech Phone: +1.4806242599
Tech Phone Ext:
Tech Fax: +1.4806242598
Tech Fax Ext:
Tech Email: Select Contact Domain Holder link at https://www.godaddy.com/whois/results.aspx?domain=HASHCAT.NET
Name Server: NS03.DOMAINCONTROL.COM
Name Server: NS04.DOMAINCONTROL.COM
DNSSEC: unsigned
URL of the ICANN WHOIS Data Problem Reporting System: http://wdprs.internic.net/
>>> Last update of WHOIS database: 2022-06-17T07:20:06Z <<<
For more information on Whois status codes, please visit https://icann.org/epp
TERMS OF USE: The data contained in this registrar's Whois database, while believed by the
registrar to be reliable, is provided "as is" with no guarantee or warranties regarding its
accuracy. This information is provided for the sole purpose of assisting you in obtaining
information about domain name registration records. Any use of this data for any other purpose
is expressly forbidden without the prior written permission of this registrar. By submitting
an inquiry, you agree to these terms and limitations of warranty. In particular, you agree not
to use this data to allow, enable, or otherwise support the dissemination or collection of this
data, in part or in its entirety, for any purpose, such as transmission by e-mail, telephone,
postal mail, facsimile or other means of mass unsolicited, commercial advertising or solicitations
of any kind, including spam. You further agree not to use this data to enable high volume, automated
or robotic electronic processes designed to collect or compile this data for any purpose, including
mining this data for your own personal or commercial purposes. Failure to comply with these terms
may result in termination of access to the Whois database. These terms may be subject to modification
at any time without notice.
 217.160.0.105
217.160.0.105
 United States
United States
 Valid SSL
Valid SSL