Metasploit | Penetration Testing Software, Pen Testing Security | Metasploit
Find security issues, verify vulnerability mitigations & manage security assessments with Metasploit. Get the world's best penetration testing software now.
Stats
Alexa Rank:
Popular in Country:
Country Alexa Rank:
language: en
Response Time: 0.045946
SSL: Enable
Status: up
Code To Txt Ratio
Word Count 344
Links
ratio 47.031327250663
SSL Details
SSL Issuer:
Issuer: Amazon
Valid From: 2021-09-14 00:00:00
Expiration Date: 2022-10-13 23:59:59
SSL Organization:
Signature ca11c0e71fa5c5752de5d654d0c8e559b6044e1e
Algorithm: RSA-SHA256
Found 72 Top Alternative to Metasploit.com

 Rapid7.com
Rapid7.com
Cybersecurity & Compliance Solutions & Services | Rapid7
Supercharge your security impact with Rapid7, delivering shared visibility, analytics, and automation to unite security, IT, and DevOps teams.
 Nmap.org
Nmap.org
Nmap: the Network Mapper - Free Security Scanner
Nmap Free Security Scanner, Port Scanner, & Network Exploration Tool. Download open source software for Linux, Windows, UNIX, FreeBSD, etc.

 Pentestbox.org
Pentestbox.org
Pentest Box
PentestBox is an Opensource PreConfigured Portable Penetration Testing Environment for the Windows Operating System.

 Netsparker.com
Netsparker.com
Invicti | Web Application Security For Enterprise
Get accurate, automated application security testing that scales like no other solution. Secure 1000s of web assets with less manual effort. Reduce your risk with the only…

 Kali.org
Kali.org
Kali Linux | Penetration Testing and Ethical Hacking Linux Distribution
Home of Kali Linux, an Advanced Penetration Testing Linux distribution used for Penetration Testing, Ethical Hacking and network security assessments.
 Scriptjunkie.us
Scriptjunkie.us
Thoughts on Security
schadnfreude Posted by scriptjunkie in Uncategorized on November 5, 2021 You’ll be happy when they can’t spy on you. 🔒 🕵 👨👩👧👦 📞 🎥 📂 🖧 🛡 Schadnfreude is a new end-to-end encrypted, anonymous ID and IP-hiding, decentralized, audio/video/file sharing/offline messaging multi-device platform built for both communications and application security...

 Cobaltstrike.com
Cobaltstrike.com
Cobalt Strike | Adversary Simulation and Red Team Operations
Cobalt Strike in an adversary simulation tool that can emulate the tactics and techniques of a quiet long-term embedded threat actor in an IT network using Beacon, a post-exploitation agent and covert channels.


 Vulnhub.com
Vulnhub.com
Vulnerable By Design ~ VulnHub
VulnHub provides materials allowing anyone to gain practical hands-on experience with digital security, computer applications and network administration tasks.

 Pentestgeek.com
Pentestgeek.com
Learn Web Application Penetration Testing - Pentest Geek
HACK LIKE A PRO. SECURE LIKE A BOSS. Are you an Ethical Hacker? Do you want to be one? This course will teach you everything you need to know to get started now! I'M READY TO LEARN Hackers and Penetration Testers have one thing in common. They know how to...
 Pentestlab.blog
Pentestlab.blog
Penetration Testing Lab – Offensive Techniques & Methodologies
Offensive Techniques & Methodologies
 Adeptus-mechanicus.com
Adeptus-mechanicus.com
Main
"Turning and turning in the widening gyre The falcon cannot hear the falconer; Things fall apart; the centre cannot hold; Mere anarchy is loosed upon the world, The blood-dimmed tide is loosed, and everywhere The ceremony of innocence is drowned; The best lack all conviction, while the worst Are full...

 Portswigger.net
Portswigger.net
Web Application Security, Testing, & Scanning - PortSwigger
PortSwigger offers tools for web application security, testing, & scanning. Choose from a range of security tools, & identify the very latest vulnerabilities.
 Didierstevens.com
Didierstevens.com
Didier Stevens
-----BEGIN PGP PUBLIC KEY BLOCK----- Version: GnuPG v1.4.7 (MingW32) mQGiBEcg+PERBAC7Zex85WF3yfmGOfGjAMLsNx6y39rrmUjtNeGdHaFOS+RO2KQ9 19sXx5V42BVtsDae5qGFkAfdYi9uWiTiPHI4C3JXSnsVx1IHd4/Hr4vC/rncSwe/ emajuorUJwAB3FmWQm2lzSuS6FJNzpARGMH4X15O+dFy0pr0nJ79IFPO8wCghM5S yA8vcSvCDJ8bsKHruIpyN6MD/0GMNI3wK3Pb5OVJFDxVWQLrMaA8gdQBTiZ42aW+ 2rsyr1d61e94Nvurs0FwohzllfPyjX+NuiWcjlho2jnpkUO/iC/HcNzCAi3qN2Vv q6EfL8r7XVy/lG+OGhvYSnQU2GZjJyIltYjyKyhHD5P2GlBu9BSqN06bFgOdXcmB Bgb4A/9BqxOx8a+X3GiV1H+dnNfL7jS2CoH43Z3aXYCWgqMxEuvXvIrIPa6XAYNo /F5UGkONknBjxC/Pr9w/jORC8oW0AYZJlHmpTQOHedgsrCBPXmyYSu/pafS6O2V9 w5BGLpkmTQAX/Hr/DuGD0JGqVcOvGhVAgcrdBxDfEMNti+Lbw7QpRGlkaWVyIFN0 ZXZlbnMgPGRpZGllci5zdGV2ZW5zQGdtYWlsLmNvbT6IYAQTEQIAIAUCRyD48QIb AwYLCQgHAwIEFQIIAwQWAgMBAh4BAheAAAoJEHdz1uvbYxaW5iwAnRJp2jEfQ6h7 cvv4VT86VG6QzBzzAJ9l1FLWhOHDofRUAhZdYSLZjnURSbkCDQRHIPjxEAgAt21C uJWdsVbhnOOO/bfMuQOUrceh0DUDuO76QWrQSxz/vFSrVxBtSKct9GTICEk+3GXQ I1pmuxkAYcr3J1G36bKoPnMyX7x/+tJC+WkoroKzTVMlahdFjmI04Tc8iBYTwROn 8i6J5l9hoaNKLKfdV6Xmw0Y7A9w9wVRo09NkJiSzff3iQbis0mrh/jxup1coa4L+ 4FBjIHztt+7LXfwqKqBM1OnXvLPlSTJT4/KjRnCdNDy+zxz6g6Yzy4NNTcP0+EFr CijuE7/jLZho6P79Qt2nfe2O9BTQW6jIFaF2guvGMsEqgX9MtWxnd+P7KSz+1CtL sYkfiEdF8qp8ubHiswADBQf/XuRea1pMXKUs3f//Y7GRWtm2s9jPY5uSYqY7XaOm lsEflToedo8KxfymgA3axyI2QwxTEBnanPJQdPPd/vBSBCKmp5ihsFcKO30AKtbC J5SFRzTJmjwtaSRjI4CMZbIJCjb7uCSzF6ylEGIBypt+MbBXEhmGsv886Sm5PpR/ vXfZdtzFxMILJ8wgxSh5wtQ+rZHZUsPRszb45fUuaSPquStpndqp/Stx14s1LfGg Inpxn3eh+sz6iksaIb9mDZ5jcuRTx9rH43TkZRpdvk3WIHBo/6YFdOZUEhzKLYnO Fmjssq5wXIt2inj+C6H9kgLOYhb+bj8+GbdNhQT5oXH4EIhJBBgRAgAJBQJHIPjx AhsMAAoJEHdz1uvbYxaWAWoAoIH4MxPReBq32E2gmqrzOXXcL6BkAJ9L6FXNh9pH x7z8V6php7uMJQX6UA== =8AJk -----END PGP PUBLIC KEY BLOCK-----

 Acunetix.com
Acunetix.com
Acunetix | Web Application Security Scanner
Acunetix is an end-to-end web security scanner that offers a 360 view of an organization’s security. Allowing you to take control of the security of all you web applications, web services, and APIs to ensure long-term protection. Acunetix’s scanning engine is globally known and trusted for its unbeatable speed and precision.

 Owasp.org
Owasp.org
OWASP Foundation | Open Source Foundation for Application Security
OWASP Foundation, the Open Source Foundation for Application Security on the main website for The OWASP Foundation. OWASP is a nonprofit foundation that works to improve the security of software.

 Sans.org
Sans.org
Cyber Security Training | SANS Courses, Certifications & Research
SANS Institute is the most trusted resource for cybersecurity training, certifications and research. Offering more than 60 courses across all practice areas, SANS trains over 40,000 cybersecurity professionals annually.
 Securitytraning.com
Securitytraning.com
securitytraning.com is for sale | HugeDomains
Get this domain name before someone else does. Quick and painless shopping. Affordable payment options available.
 Hacking-tutorial.com
Hacking-tutorial.com
Ethical Hacking Tutorials, Tips and Tricks - Free Tutorials, Tools, How to's
Ethical Hacking Tutorial, Tips and Trick. Free hacking knowledge, learn how to hack

 Blueliv.com
Blueliv.com
Cyber Threat Intelligence Solution | Outpost24
Our Cyber Threat Intelligence solution helps you counter real-time cyberthreats faster using our adaptive, modular technology, Threat Compass.
 Sectools.org
Sectools.org
SecTools.Org Top Network Security Tools
Rankings and reviews of computer and network security software, programs, and tools.

 Hakin9.org
Hakin9.org
Home - Hakin9 - IT Security Magazine
Our tutorials, case studies and online courses will prepare you for the upcoming, potential threats in the cyber security world.

 Coresecurity.com
Coresecurity.com
Core Security | Cyber Threat Prevention & Identity Governance
Contact Us Support All HelpSystems Products FREE TRIALS Contact Us Support All HelpSystems Products FREE TRIALS Cyber Threat Toggle Dropdown Products Core Impact Penetration testing software Cobalt Strike Red team software Event Manager Security information and event management Network Insight Network Traffic Analysis Powertech Antivirus Server-level virus protection Security Auditor...
 Hydrasky.com
Hydrasky.com
All things in moderation – We are local security
+ UAC BYPASS VIA DOTNET PROFILER ON WINDOWS 10 Vulnerabilities and Exploits In the previous post, we know how to use Registry Hijacking to bypass UAC on Windows 10. Today, we continue to do that with different technique with … By Stephen Stinson May 20, 2020 + + UAC Bypass Via...

 Yeahhub.com
Yeahhub.com
Yeah Hub - Kali Linux Tutorials | Tech News | SEO Tips and Tricks
Kali Linux Tutorials | Tech News | SEO Tips and Tricks

 Cyberpratibha.com
Cyberpratibha.com
Cyber Pratibha | Enhance Cyber Skills
One Step Towards, Secure Cyber Word It's your turn to help to secure cyber space by enhancing your technical skills including Expertise in Linux, Wireless Security, Advanced in Kali Linux, Ethical Hacking and more Start Your Journy Work as volunteer Online Classes One to one, One to many classes make you | Cyber Pratibha

 Hackingtools.in
Hackingtools.in
Hacking Trainer - Ethical Hacking Training in Hyderabad
Hacking Trainer is a unit of BERRY9 IT SERVICES Pvt. Ltd and EC-Council ATC. We offer Ethical Hacking Training and InfoSec Certifications.
 Faradaysec.com
Faradaysec.com
Faraday Security - Protect your business, scale your security.
Optimize your network security posture with our Cybersecurity tools. Reinforce your network security and protect from attackers.
 E-spincorp.com
E-spincorp.com
Homepage | E-SPIN Group
Leaders In Technologies With more than 17 years in enterprise technology solutions we are the leaders in this industry! SOLUTIONS PRODUCTS Distribution & Trading Our team is best to co ordinate and work with supplier, channel, corporate & government client. SOLUTIONS PRODUCTS Cyber Security From Enterprise Threat and Vulnerability Management,...

 Backtrack-linux.org
Backtrack-linux.org
BackTrack Linux - Penetration Testing Distribution
BackTrack Linux was 2006-2013. Now reborn as Kali Linux

 Parrotsec.org
Parrotsec.org
Parrot Security
ParrotSEC The operating system for | The ultimate framework for your Cyber Security operations Download Get Started What's new in ParrotOS 5.0 Electro Ara Tools for every operation Choose between 600+ tools for every kind of Red and Blue team operation. Parrot Security provides a huge arsenal of tools, utilities...
 Cybervie.com
Cybervie.com
Best Cyber Security Training and Certified Courses | Cybervie
Cybervie is an Indian company, started in 2017 located in Hyderabad & provides all forms of cybersecurity training to make your career.

 Kalilinuxtutorials.com
Kalilinuxtutorials.com
Kali Linux Tutorials - A Single Stop for Kali Linux Tools
Kali Linux tutorials is an independent platform that covers step by tutorials, advanced penetration testing, Ethical Hacking and network security tools.
 Securityonline.info
Securityonline.info
Penetration Testing • Information Security
Securityonline is a huge security community. It is committed to the sharing of high-quality technical articles and safety reports, focusing on high-quality security and security incidents in the industry.
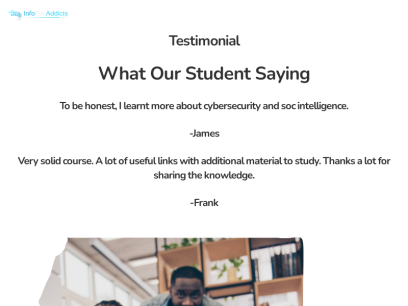
 Infosecaddicts.com
Infosecaddicts.com
Online Training - Infosecaddicts
Testimonial What Our Student Saying To be honest, I learnt more about cybersecurity and soc intelligence. -James Very solid course. A lot of useful links with additional material to study. Thanks a lot for sharing the knowledge. -Frank 50 k Finished Sessions 70 k+ Enrolled Learners 120 + Online Instructors 100 % Satisfaction Rate Contact...

 Packetstormsecurity.net
Packetstormsecurity.net
Packet Storm
Information Security Services, News, Files, Tools, Exploits, Advisories and Whitepapers
 Samsclass.info
Samsclass.info
samsclass.info: Sam Bowne Class Information
Pacific Hackers IhackNFT - Cryptocurrency CTF Fri, July 15, 2022, 9:00 AM - 5:00 PM PDT Hacker Dojo 855 Maude Ave · Mountain View, CA HOPE 2022 July 22-24, 2022 New York City Approved Workshops Violent Python 3 · Friday 22-July-2022, 12:00-15:00 · Workshop B Threat Hunting with Splunk ·...

 Exploitpack.com
Exploitpack.com
Exploit Pack
Monthly subscription €200 Per Month - (1 user license) ✔ 39.000+ exploits ✖ Zero day exploits ✔ Adversary simulations ✔ Remote and local Fuzzer ✔ Web attacks ✔ Post-Exploitation ✔ Remote control ✔ Auto attacks ✔ Network scanner ✔ Targets management ✔ Hexa editor ✔ Reverse shells ✖ Live monthly...
 Concise-courses.com
Concise-courses.com
Resource For Hacker Tools & Growth / SEO Hacking Tools
Site Dedicated To Intrepid SEO Explorers

 Attackresearch.com
Attackresearch.com
Attack Research - Attack Research, LLC - Advanced Computer Security Research and Consulting
ATTACK SIMULATION We go far beyond standard tools and scripted tests. Find out if your network or technology can stand real-world and dedicated attackers. Specialized Industries Attack Research specializes in industries that use unconventional configurations. We have vast experience with avionics, automotive, military, SATCOM, and SCADA systems. TRAINING Learn our...

 Wordpress.com
Wordpress.com
WordPress.com: Fast, Secure Managed WordPress Hosting
Create a free website or build a blog with ease on WordPress.com. Dozens of free, customizable, mobile-ready designs and themes. Free hosting and support.


 Kalitutorials.net
Kalitutorials.net
Kali Linux Hacking Tutorials
Thursday, December 6, 2018 Bypassing website blocking/censorship with Secure DNS and Encrypted SNI (cloudflare only) By Shashwat December 06, 2018 blocking, bypassing, censorship, cloudflare, esni, firefox, nightly, tls, tls1.3 Disclaimer - TLDR; some stuff here can be used to carry out illegal activity, our intention is, however, to educate I...

 Hackercool.com
Hackercool.com
Hackercool Magazine - Ethical Hacking Magazine for hackers
Hacking Magazine with a difference. That's what Hackercool Magazine is. Learn Blackhat hacking. is a cyber security monthly magazine that

 Khromozome.com
Khromozome.com
久久婷香五月综合色啪,手机国产乱子伦精品视频,免费人成在线观看网站,AV男人的天堂在线观看第三区!
久久婷香五月综合色啪,手机国产乱子伦精品视频,免费人成在线观看网站,AV男人的天堂在线观看第三区,av资源网,免费三级片网站,三级 经典在线视频¶«Ý¸ÊÐÓÅÆæ°ü×°,ΪµØ·½¾ÓÍ»¯¹¤¼¯ÍŹ«Ë¾ËùÊôµÄ,ÒÔÁ¶Óͺͻ¯¹¤¹¤³ÌÉè¼ÆΪÖ÷Ìå,¿ÉʵʩÊÇÊÀ½ç500Ç¿ÖйúÖÐÌú¹É·ÝÓÐÏÞ¹«Ë¾µÄ¹Ç¸É³ÉÔ±ÆóÒµ¡£1978Äê5Ô£¬ÏíÆóÒµÃûƬ: »ù±¾ÐÅÏ¢ ÆóÒµÃû³ÆÕã¹úÎñ¹¤³Ì½¨Éè×ܳаüºÍ¹¤³ÌÏî¼Ã×ö³öÖØÒª¹±Ïס£ ¾ÁÁúÖ½ÖÆÆ·ÓÐÏÞ¹«Ë¾×ùÂäÓÚ·ç¾°ÐãÀö

 Cursodehackers.com
Cursodehackers.com
Curso de hackers
Curso gratuito para aprender a ser un hacker, la web para aprender a hackear y de seguridad informática donde hackear facebook, wifi, contraseñas y muchas otras cosas de forma sencilla
Technologies Used by metasploit.com
Dns Records of metasploit.com
A Record: 13.227.219.129 13.227.219.76 13.227.219.83 13.227.219.69AAAA Record:
CNAME Record:
NS Record: ns-290.awsdns-36.com ns-1709.awsdns-21.co.uk ns-1441.awsdns-52.org ns-627.awsdns-14.net
SOA Record: awsdns-hostmaster.amazon.com
MX Record: alt1.aspmx.l.google.com alt4.aspmx.l.google.com alt3.aspmx.l.google.com aspmx.l.google.com alt2.aspmx.l.google.com
SRV Record:
TXT Record: msu7hdpr3s9t605hgk30nulv61 google-site-verification=3c5G707h36r_fLqn_xjqIXpiZ8PXrb12BD7YHTNpU-I MS=ms22912677 v=spf1 a include:_spf.google.com include:spf.protection.outlook.com -all
DNSKEY Record:
CAA Record:
Whois Detail of metasploit.com
Domain Name: metasploit.comRegistry Domain ID: 98973533_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.markmonitor.com
Registrar URL: http://www.markmonitor.com
Updated Date: 2022-05-09T09:45:37+0000
Creation Date: 2003-06-10T06:53:17+0000
Registrar Registration Expiration Date: 2024-06-10T00:00:00+0000
Registrar: MarkMonitor, Inc.
Registrar IANA ID: 292
Registrar Abuse Contact Email: [email protected]
Registrar Abuse Contact Phone: +1.2086851750
Domain Status: clientUpdateProhibited (https://www.icann.org/epp#clientUpdateProhibited)
Domain Status: clientTransferProhibited (https://www.icann.org/epp#clientTransferProhibited)
Domain Status: clientDeleteProhibited (https://www.icann.org/epp#clientDeleteProhibited)
Registrant Organization: Rapid7
Registrant State/Province: MA
Registrant Country: US
Registrant Email: Select Request Email Form at https://domains.markmonitor.com/whois/metasploit.com
Admin Organization: Rapid7
Admin State/Province: MA
Admin Country: US
Admin Email: Select Request Email Form at https://domains.markmonitor.com/whois/metasploit.com
Tech Organization: Rapid7
Tech State/Province: MA
Tech Country: US
Tech Email: Select Request Email Form at https://domains.markmonitor.com/whois/metasploit.com
Name Server: ns-1441.awsdns-52.org
Name Server: ns-290.awsdns-36.com
Name Server: ns-1709.awsdns-21.co.uk
Name Server: ns-627.awsdns-14.net
DNSSEC: unsigned
URL of the ICANN WHOIS Data Problem Reporting System: http://wdprs.internic.net/
>>> Last update of WHOIS database: 2022-06-28T20:15:01+0000 <<<
For more information on WHOIS status codes, please visit:
https://www.icann.org/resources/pages/epp-status-codes
If you wish to contact this domain’s Registrant, Administrative, or Technical
contact, and such email address is not visible above, you may do so via our web
form, pursuant to ICANN’s Temporary Specification. To verify that you are not a
robot, please enter your email address to receive a link to a page that
facilitates email communication with the relevant contact(s).
Web-based WHOIS:
https://domains.markmonitor.com/whois
If you have a legitimate interest in viewing the non-public WHOIS details, send
your request and the reasons for your request to [email protected]
and specify the domain name in the subject line. We will review that request and
may ask for supporting documentation and explanation.
The data in MarkMonitor’s WHOIS database is provided for information purposes,
and to assist persons in obtaining information about or related to a domain
name’s registration record. While MarkMonitor believes the data to be accurate,
the data is provided "as is" with no guarantee or warranties regarding its
accuracy.
By submitting a WHOIS query, you agree that you will use this data only for
lawful purposes and that, under no circumstances will you use this data to:
(1) allow, enable, or otherwise support the transmission by email, telephone,
or facsimile of mass, unsolicited, commercial advertising, or spam; or
(2) enable high volume, automated, or electronic processes that send queries,
data, or email to MarkMonitor (or its systems) or the domain name contacts (or
its systems).
MarkMonitor reserves the right to modify these terms at any time.
By submitting this query, you agree to abide by this policy.
MarkMonitor Domain Management(TM)
Protecting companies and consumers in a digital world.
Visit MarkMonitor at https://www.markmonitor.com
Contact us at +1.8007459229
In Europe, at +44.02032062220
--

 192.124.249.5
192.124.249.5
 United States
United States
 Valid SSL
Valid SSL