Hacking Tutorials by Xeus
The most up to date ethical hacking tutorials and cyber security news.
Stats
Alexa Rank:
Popular in Country:
Country Alexa Rank:
language: en
Response Time: 0.364245
SSL: Enable
Status: up
Code To Txt Ratio
Word Count 361
Links
ratio 10.952252495279
SSL Details
SSL Issuer:
Issuer: R3
Valid From: 2022-06-07 13:49:11
Expiration Date: 2022-09-05 13:49:10
SSL Organization:
Signature 28b85cd296c09cd96e644833a0de5f86b7cd4017
Algorithm: RSA-SHA256
Found 67 Top Alternative to Xeushack.com
 Hacking-tutorial.com
Hacking-tutorial.com
Ethical Hacking Tutorials, Tips and Tricks - Free Tutorials, Tools, How to's
Ethical Hacking Tutorial, Tips and Trick. Free hacking knowledge, learn how to hack

 Edge-security.com
Edge-security.com
Edge-security Cybersecurity services
Open source tools Security tools We have created tools used by thousands of professionals on their daily jobs, included in all Security distributions like Kali Linux. Come and check them out! Learn More
 Securitytraning.com
Securitytraning.com
securitytraning.com is for sale | HugeDomains
Get this domain name before someone else does. Quick and painless shopping. Affordable payment options available.
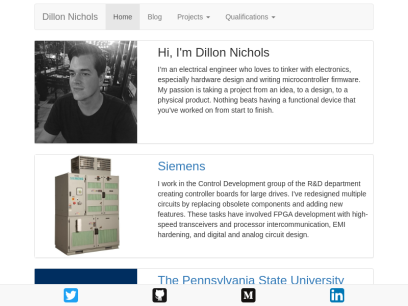
 Tinkerer.us
Tinkerer.us
Dillon Nichols
Toggle navigation Dillon Nichols Home Blog Projects MSP430 Reaction Game Homebrew Gameboy Cartridge #Makevember 2017 #Makevember 2019 External Projects Qualifications Penn State Education Engineering Experiences Hi, I'm Dillon Nichols I’m an electrical engineer who loves to tinker with electronics, especially hardware design and writing microcontroller firmware. My passion is taking...
 Hempstutorials.co.uk
Hempstutorials.co.uk
Security Tutorials - Keeping Cyber Security Simple
Keeping Cyber Security Simple

 Opendatasecurity.io
Opendatasecurity.io
Open Data Security | Servicios y Soluciones de Ciberseguridad
Audite sus infraestructuras y forme a sus empleados con nosotros para evitar ser víctima de un ciberataque. Prestamos servicios a empresas y organizaciones.

 Wordpress.com
Wordpress.com
WordPress.com: Fast, Secure Managed WordPress Hosting
Create a free website or build a blog with ease on WordPress.com. Dozens of free, customizable, mobile-ready designs and themes. Free hosting and support.

 Hackingloops.com
Hackingloops.com
Learn Ethical Hacking and Penetration Testing Online | Learn ethical hacking, penetration testing, cyber security, best security and web penetration testing techniques from best ethical hackers in security field.
Learn ethical hacking, penetration testing, cyber security, best security and web penetration testing techniques from best ethical hackers in security field.
 Ajithsmokie.blogspot.com
Ajithsmokie.blogspot.com
BlogBits
Blogbits is from chennai and teach you many good stuffs like installing Computer Software.From the upcoming post you will learn about hacking
 Adaywithtape.blogspot.com
Adaywithtape.blogspot.com
A day with Tape
1) probemon.sh The main script to monitor for WiFi probes, write backup files after reaching a certain size and logging restarts of the script. #!/usr/bin/bash DIR="/root/probemon/" # Directory for the working file and logs PROBELOG=probemon.txt # Working...
 Hackinglikeapro.blogspot.com
Hackinglikeapro.blogspot.com
HACKING LIKE A PRO
Friday, 28 April 2017 Tricks New How to control your Pc/Laptop from anywhere Rahul UK 17:12 20 Comments Want to impress your friend? Want to spy on your PC/Laptop? Want to use your PC/Laptop from anywhere in the world. Then you are ... Read More Read more 20 comments: By...
 Deepweb-sites.com
Deepweb-sites.com
Deep Web Sites 2022 | Dark Web | Deep Web Links | Hidden Wiki
The Deep Web Sites, Dark web, Hidden Wiki is accessed using Tor that contains .onion websites and provided Deep Web Links 2022 with more of deep web news.
 Ethicalhackx.com
Ethicalhackx.com
Ethical Hacking Tutorials - Learn Ethical Hacking, Pentesting , Linux
Ethical Hacking Tutorials - Learn Ethical Hacking, Pentesting, Website Hacking, Linux and Windows Hacking, Free EBooks and Software Downloads
 Hackersonlineclub.com
Hackersonlineclub.com
Homepage - HackersOnlineClub
HackersOnlineClub is leading Cyber Security Tutorial Website. Learn Penetration Testing, Bug Bounty Tips, and Infosec Courses.

 Hemendra-blackhathacker.blogspot.com
Hemendra-blackhathacker.blogspot.com
black hat hacker
Saturday, 25 February 2012 IRRITATING PRANK hi everyone i was fealing very bore so i just now made a very annoying virus. it can irritate any one okay the code i m giving is of dos, so save it with an extension of .bat copy dis code and save it as a batch file...
 Cehacks.blogspot.com
Cehacks.blogspot.com
Computer Expert Hackers
How to Hack a Website in Backtrack / Kali Linux By: R3dRyD3r on 1:21 PM Hack a Website in Backtrack / Kali Linux Kali Linux / Backtrack First off, you need to have Kali linux (or backtrack) up and running on your machine. Any other Linux distro might work, but...
 Gobruen.com
Gobruen.com
Useful Information: tons of info stuffed into a small site
important.articles(this_site) ------------------------------ /os: move contacts on one PDA to another /net: stop junk mail, for real /hw: build your own pc /db/sql: oracle-sqlplus cheatsheet and glossary /progs: c++ file i/o /os: fix svchost damage from blaster virus recently.expanded/added ---------------------- lisp security javascript xml intro to c++ headers dos ...
 Macspoofer.com
Macspoofer.com
MacSpoofer
Change your MAC address the way you like it! It's very easy to use. Supports Mac Os X 10.6 and above (Including Os X Lion).
 Evestigate.com
Evestigate.com
Global Digital Forensics | Cybersecurity | eDiscovery
Global Digital Forensics is a top national provider of digital forensics, eDiscovery and cybersecurity services. Experienced and certified experts.
 Corrupt.wiki
Corrupt.wiki
Introduction - Corrupt.wiki
Please note that this wiki is still heavily in development. Videogame Corruptions or the act of "corrupting games" is taking a video game and breaking it using whatever means necessary, usually with a program called a corruptor. This software can either modify the bytes in a ROM or a game's...
 Dsasmblr.com
Dsasmblr.com
DSASMBLR
Welcome to DSASMBLR: Video game journalism, hacking, and programming by Stephen Chapman. Start Here! Welcome to DSASMBLR: Video game journalism, hacking, and programming by Stephen Chapman. Start Here!

 Scottschober.com
Scottschober.com
Home - Scott Schober
Scott Schober is a cybersecurity expert, presenter, author and CEO of BVS, a successful security tech company
 Theprohack.com
Theprohack.com
Pro Hack
A leading computer security and technology blog that offers hacks,security and technology news,hacking tools,tutorials and gaming reviews.

 Mightyshouts.com
Mightyshouts.com
mightyshouts.com is for sale | HugeDomains
100% satisfaction guaranteed. Hassle-free shopping. We help you find the right domain name.
 Rootsh3ll.com
Rootsh3ll.com
welcome to rootsh3ll
Learn Penetration Testing by practice... A massive brute-force attack hit our application server in mid-2018, with around 500,000 login attempts at peak in just one day. That's massive, and we wouldn't have survived if we didn't have the necessary security implementations in the system beforehand. Simply put, we hacked our...

 Kalitutorials.net
Kalitutorials.net
Kali Linux Hacking Tutorials
Thursday, December 6, 2018 Bypassing website blocking/censorship with Secure DNS and Encrypted SNI (cloudflare only) By Shashwat December 06, 2018 blocking, bypassing, censorship, cloudflare, esni, firefox, nightly, tls, tls1.3 Disclaimer - TLDR; some stuff here can be used to carry out illegal activity, our intention is, however, to educate I...
 Concise-courses.com
Concise-courses.com
Resource For Hacker Tools & Growth / SEO Hacking Tools
Site Dedicated To Intrepid SEO Explorers

 Wintertree-software.com
Wintertree-software.com
Spell check, thesaurus, and grammar engines, components, controls, libraries, SDKs, and source code for Visual Basic, ASP, HTML Web forms, Java, ActiveX.
Spell check, thesaurus, and grammar check software for Visual Basic, Java, MFC, Windows, UNIX/Linux, Web/HTML, ASP, and CGI developers.

 Rivalhost.com
Rivalhost.com
Fully Managed Web Hosting, Cloud & VPS Hosting | Rivalhost
Take advantage of high-performance managed web hosting services by a global, leading edge provider of web hosting solutions. Contact Rivalhost now.
 Technitium.com
Technitium.com
Technitium | Push The Limits
Technitium provides software for privacy over the Internet. Technitium MAC Address Changer (TMAC) is a freeware utility to instantly change or spoof MAC Address of any network card (NIC). Technitium Bit Chat is a secure, peer-to-peer, open source instant messenger that is designed to provide end-to-end encryption for privacy using strong cryptography.
 Sectools.org
Sectools.org
SecTools.Org Top Network Security Tools
Rankings and reviews of computer and network security software, programs, and tools.

 Steve-jansen.github.io
Steve-jansen.github.io
/* steve jansen */
The Jenkins credentials-binding plugin provides a convenient way to securely store secrets like usernames/passwords in Jenkins. You can even inject …
 Spyboy.blog
Spyboy.blog
Spyboy blog – Learn ethical hacking , networking, social engineering, cyber security, pen-testing, linux, android windows tricks.
Learn ethical hacking , networking, social engineering, cyber security, pen-testing, linux, android windows tricks.

 Bonkersabouttech.com
Bonkersabouttech.com
What Is Chrome’s Omnibox? (Plus Tips And Tricks) Let me fill you in on a little secret if you’re using Google Chrome or any of the other Chromium-based […] Best Bluetooth Ceiling Speakers (Without Choice Overload) Featured image credit: Flickr/Paul Long Bluetooth soundbars and portable speakers have been all the...
 Hsploit.com
Hsploit.com
HackerSploit Blog - Cybersecurity Training & Penetration Testing
HackerSploit is the leading provider of free Infosec and cybersecurity training. Our goal is to make cybersecurity training more effective and accessible to students and professionals. We achieve this by providing essential training on how to attack and defend systems with virtual labs and real-world scenarios. We offer individual and corporate training packages in Penetration Testing & Red Team Operations, Web application penetration testing, and cybersecurity awareness training.
 Cybervie.com
Cybervie.com
Best Cyber Security Training and Certified Courses | Cybervie
Cybervie is an Indian company, started in 2017 located in Hyderabad & provides all forms of cybersecurity training to make your career.
 Opentechinfo.com
Opentechinfo.com
Opentech Info - Tech Tips & Tricks
The opentechinfo blog is a tech blog. Where you can find tutorial and knowledge related to android, hacking. My blog is basically a go-to guide about these topics.


 Thehacktoday.com
Thehacktoday.com
Hack Today | Hacking News Platform that covers on Cyber Security, Privacy, Surveillance and Cyber Crime.
Hack Today is a News Platform that centers on InfoSec, Cyber Crime, Privacy, Surveillance and Hacking News with full-scale reviews on Social Media Platforms & Technology trends.

 Hackingvision.com
Hackingvision.com
HackingVision – Ethical Hacking Tutorials, Tips & Tricks, Kali Linux, Beginners Hacking
Top Colleges for Cybersecurity Degree Programs 1st June 2022 by Carl Hill Cybersecurity has a great job market with many job vacancies and attractive salaries. When you have a cybersecurity degree, you can easily find job opportunities such as security engineers. Therefore, training begins at the college level when you...
 Pentestlab.blog
Pentestlab.blog
Penetration Testing Lab – Offensive Techniques & Methodologies
Offensive Techniques & Methodologies
 Dephace.com
Dephace.com
HugeDomains.com
dephace.com is for sale Please prove you're not a robot View Price Processing

 Picateshackz.com
Picateshackz.com
PicateShackZ.com is for sale | HugeDomains
Find your domain name at HugeDomains. Start using this domain right away.

 Allabouttesting.org
Allabouttesting.org
All About Testing - Software Testing & Ethical Hacking Fundamentals
Our website's aims to provide quality content on various topics related to fundamentals of software testing & ethical hacking.
 Kennyvn.com
Kennyvn.com
Kali Linux Tutorials - Kennyvn
A blog dedicated to sharing actionable Kali Linux tutorials, guides, cheatsheets, and tips and tricks.
 Kalitut.com
Kalitut.com
KaliTut Linux and pentesting blog - KaliTut
Windows PowerShell tutorial for beginners Detailed PowerShell tutorial for beginners! ✓ Create and run PowerShell script, practice-oriented knowledge about PowerShell. Learn to Hack Steps from Beginner to Hacker Learn to hack , Beginner's Guide - with some many Tutorials on how to Hack Computers with Kali Install Linux PowerShell Tutorial...
 Darknet.org.uk
Darknet.org.uk
Darknet - Hacking Tools, Hacker News & Cyber Security
Darknet is your best source for the latest hacking tools, hacker news, cyber security best practices, ethical hacking & pen-testing.
 Makesfit.com
Makesfit.com
Makesfit - Best Reviews & Guides For Top Tech Products
Best Reviews & Guides For Top Tech Products

 Khromozome.com
Khromozome.com
久久婷香五月综合色啪,手机国产乱子伦精品视频,免费人成在线观看网站,AV男人的天堂在线观看第三区!
久久婷香五月综合色啪,手机国产乱子伦精品视频,免费人成在线观看网站,AV男人的天堂在线观看第三区,av资源网,免费三级片网站,三级 经典在线视频¶«Ý¸ÊÐÓÅÆæ°ü×°,ΪµØ·½¾ÓÍ»¯¹¤¼¯ÍŹ«Ë¾ËùÊôµÄ,ÒÔÁ¶Óͺͻ¯¹¤¹¤³ÌÉè¼ÆΪÖ÷Ìå,¿ÉʵʩÊÇÊÀ½ç500Ç¿ÖйúÖÐÌú¹É·ÝÓÐÏÞ¹«Ë¾µÄ¹Ç¸É³ÉÔ±ÆóÒµ¡£1978Äê5Ô£¬ÏíÆóÒµÃûƬ: »ù±¾ÐÅÏ¢ ÆóÒµÃû³ÆÕã¹úÎñ¹¤³Ì½¨Éè×ܳаüºÍ¹¤³ÌÏî¼Ã×ö³öÖØÒª¹±Ïס£ ¾ÁÁúÖ½ÖÆÆ·ÓÐÏÞ¹«Ë¾×ùÂäÓÚ·ç¾°ÐãÀö
Technologies Used by xeushack.com
Dns Records of xeushack.com
A Record: 213.174.132.225AAAA Record:
CNAME Record:
NS Record: pdns01.domaincontrol.com pdns02.domaincontrol.com
SOA Record: dns.jomax.net
MX Record:
SRV Record:
TXT Record:
DNSKEY Record:
CAA Record:
Whois Detail of xeushack.com
Domain Name: xeushack.comRegistry Domain ID: 1853054379_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.godaddy.com
Registrar URL: https://www.godaddy.com
Updated Date: 2022-03-06T00:38:58Z
Creation Date: 2014-04-02T08:37:46Z
Registrar Registration Expiration Date: 2023-04-02T08:37:46Z
Registrar: GoDaddy.com, LLC
Registrar IANA ID: 146
Registrar Abuse Contact Email: [email protected]
Registrar Abuse Contact Phone: +1.4806242505
Domain Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited
Domain Status: clientUpdateProhibited https://icann.org/epp#clientUpdateProhibited
Domain Status: clientRenewProhibited https://icann.org/epp#clientRenewProhibited
Domain Status: clientDeleteProhibited https://icann.org/epp#clientDeleteProhibited
Registry Registrant ID: Not Available From Registry
Registrant Name: Registration Private
Registrant Organization: Domains By Proxy, LLC
Registrant Street: DomainsByProxy.com
Registrant Street: 2155 E Warner Rd
Registrant City: Tempe
Registrant State/Province: Arizona
Registrant Postal Code: 85284
Registrant Country: US
Registrant Phone: +1.4806242599
Registrant Phone Ext:
Registrant Fax: +1.4806242598
Registrant Fax Ext:
Registrant Email: Select Contact Domain Holder link at https://www.godaddy.com/whois/results.aspx?domain=xeushack.com
Registry Admin ID: Not Available From Registry
Admin Name: Registration Private
Admin Organization: Domains By Proxy, LLC
Admin Street: DomainsByProxy.com
Admin Street: 2155 E Warner Rd
Admin City: Tempe
Admin State/Province: Arizona
Admin Postal Code: 85284
Admin Country: US
Admin Phone: +1.4806242599
Admin Phone Ext:
Admin Fax: +1.4806242598
Admin Fax Ext:
Admin Email: Select Contact Domain Holder link at https://www.godaddy.com/whois/results.aspx?domain=xeushack.com
Registry Tech ID: Not Available From Registry
Tech Name: Registration Private
Tech Organization: Domains By Proxy, LLC
Tech Street: DomainsByProxy.com
Tech Street: 2155 E Warner Rd
Tech City: Tempe
Tech State/Province: Arizona
Tech Postal Code: 85284
Tech Country: US
Tech Phone: +1.4806242599
Tech Phone Ext:
Tech Fax: +1.4806242598
Tech Fax Ext:
Tech Email: Select Contact Domain Holder link at https://www.godaddy.com/whois/results.aspx?domain=xeushack.com
Name Server: PDNS01.DOMAINCONTROL.COM
Name Server: PDNS02.DOMAINCONTROL.COM
DNSSEC: unsigned
URL of the ICANN WHOIS Data Problem Reporting System: http://wdprs.internic.net/
>>> Last update of WHOIS database: 2022-06-15T15:31:02Z <<<
For more information on Whois status codes, please visit https://icann.org/epp
TERMS OF USE: The data contained in this registrar's Whois database, while believed by the
registrar to be reliable, is provided "as is" with no guarantee or warranties regarding its
accuracy. This information is provided for the sole purpose of assisting you in obtaining
information about domain name registration records. Any use of this data for any other purpose
is expressly forbidden without the prior written permission of this registrar. By submitting
an inquiry, you agree to these terms and limitations of warranty. In particular, you agree not
to use this data to allow, enable, or otherwise support the dissemination or collection of this
data, in part or in its entirety, for any purpose, such as transmission by e-mail, telephone,
postal mail, facsimile or other means of mass unsolicited, commercial advertising or solicitations
of any kind, including spam. You further agree not to use this data to enable high volume, automated
or robotic electronic processes designed to collect or compile this data for any purpose, including
mining this data for your own personal or commercial purposes. Failure to comply with these terms
may result in termination of access to the Whois database. These terms may be subject to modification
at any time without notice.
 103.28.12.52
103.28.12.52
 United States
United States
 Valid SSL
Valid SSL