CryptoKait – Home of the National Cyber League Player Ambassadors
CryptoKait.com Homepage

Stats
Alexa Rank: 1892317
Popular in Country:
Country Alexa Rank:
language: en
Response Time: 0.781079
SSL: Enable
Status: up
Code To Txt Ratio
Word Count 1602
Links
ratio 6.939649852081
SSL Details
SSL Issuer:
Issuer: R3
Valid From: 2022-06-11 07:36:10
Expiration Date: 2022-09-09 07:36:09
SSL Organization:
Signature 611af1878e79a7be5aeeab4f959ee99ee894e7ab
Algorithm: RSA-SHA256
Found 69 Top Alternative to Cryptokait.com


 Nationalcyberleague.org
Nationalcyberleague.org
National Cyber League
Scroll The National Cyber League Visit Cyber Skyline NCL, a community where cybersecurity is a passion! The National Cyber League (NCL) is the most inclusive, performance-based, learning-centered collegiate cybersecurity competition today! The NCL, powered by Cyber Skyline, enables students to prepare and test themselves...

 Hackinglethani.com
Hackinglethani.com
Highlighted » Hacking Lethani
Hacking Lethani Ethical Hacking Blog Highlighted Blog Entries About Lethani Contact Spanish/Español Last Post Linux Priv Esc - PwnKit (CVE-2021-4034) Proof of Concept A memory corruption has been discovered this week in PolKit, used in major Linux distributions, which allows privilege escalation. Show me Recent Posts This is the last...
 Robinverton.de
Robinverton.de
robinverton.de - red teamer, penetration tester, developer
Hey! I'm Robin. I'm working as a full-stack engineer and co-founder at prototypers and as a red teamer & pentester at Deutsche Telekom. Specialized in building: Automations and integrations Full-Stack web applications Cloud solutions (with AWS) Security tools and infrastructure Making things. Breaking things. 15+ years experience as a software...

 Hashcat.net
Hashcat.net
hashcat - advanced password recovery
World's fastest and most advanced password recovery utility

 Zsecurity.org
Zsecurity.org
zSecurity – Ethical Hacking Courses, Tutorials, News, Products and more!
Hacking Masterclass by Zaid > Zaid’s NEWEST course. > Exclusive to zSecurity. > Enrol now and get 30% off. More information 745200 Students 1013150 Followers 219 Countries Latest Posts In Hacking & Security Capstone Challenge | Linux Privilege Escalation Linux Privilege Escalation: NFS || Episode 9 DNS Spoofing Basics with...


 Wordpress.com
Wordpress.com
WordPress.com: Fast, Secure Managed WordPress Hosting
Create a free website or build a blog with ease on WordPress.com. Dozens of free, customizable, mobile-ready designs and themes. Free hosting and support.
 Rootsh3ll.com
Rootsh3ll.com
welcome to rootsh3ll
Learn Penetration Testing by practice... A massive brute-force attack hit our application server in mid-2018, with around 500,000 login attempts at peak in just one day. That's massive, and we wouldn't have survived if we didn't have the necessary security implementations in the system beforehand. Simply put, we hacked our...

 Armourinfosec.com
Armourinfosec.com
Best | Top Ethical Hacking Training Institute in Indore, India
We are offering some special modules and ethical hacking courses where students can learn IT security, ethical hacking, cyber security, network security, wireless & website security.

 Daveeargle.com
Daveeargle.com
Dave Eargle | Information Systems Management Researcher
Personal website of David Eargle
 Spycloud.com
Spycloud.com
SpyCloud | Prevent Account Takeover & Online Fraud
SpyCloud helps companies prevent account takeover & online fraud, with solutions powered by recaptured data from breaches and malware-infected devices.

 Kalilinux.in
Kalilinux.in
Best Kali Linux Tutorials
Best Place for Kali Linux Tutorials. Large number of articles on Kali Linux in easy steps from basic to advanced. Command by command with screenshots.
 Crackstation.net
Crackstation.net
CrackStation - Online Password Hash Cracking - MD5, SHA1, Linux, Rainbow Tables, etc.
Crackstation is the most effective hash cracking service. We crack: MD5, SHA1, SHA2, WPA, and much more...

 Criticalstart.com
Criticalstart.com
Managed Detection & Response and Cyber Incident Response - Critical Start
Critical Start’s industry-leading cybersecurity portfolio includes managed detection and response (MDR) services and cybersecurity consulting services.

 Passwordrecovery.io
Passwordrecovery.io
Recovery of Password from Office documents (XLSX / DOCX), ZIP files and Hashes (Cisco, SHA1, MD5)
Online service to recovery lost passwords from office documents (doc, xls) and zip files. Also, search password hashes including md5, sha1 and sha256.

 Kapaweb.gr
Kapaweb.gr
kapaweb | Domain Names | Web Hosting | IT Support | Web Development
Having a problem? We can give you simple and affordable solutions, according to your needs. Your issue is important to us! We are eager to help you

 Onlinehashcrack.com
Onlinehashcrack.com
Online Password Hash Crack - MD5 NTLM Wordpress Joomla WPA PMKID, Office, iTunes, Archive, ..
OnlineHashCrack is a powerful hash cracking and recovery online service for MD5 NTLM Wordpress Joomla SHA1 MySQL OSX WPA, PMKID, Office Docs, Archives, PDF, iTunes and more!
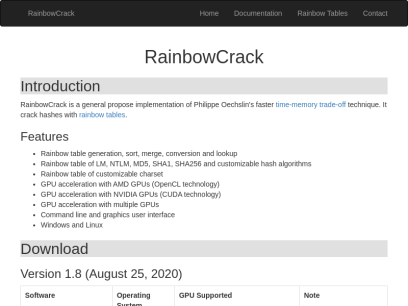
 Project-rainbowcrack.com
Project-rainbowcrack.com
RainbowCrack - Crack Hashes with Rainbow Tables
RainbowCrack Introduction RainbowCrack is a general propose implementation of Philippe Oechslin's faster time-memory trade-off technique. It crack hashes with rainbow tables. Features Rainbow table generation, sort, merge, conversion and lookup Rainbow table of LM, NTLM, MD5, SHA1, SHA256 and customizable hash algorithms Rainbow table of customizable charset GPU acceleration with...
 0xln.pw
0xln.pw
Infosec and Password Cracking Blog | Password cracking, infosec articles and assorted hackery
Password cracking, infosec articles and assorted hackery

 Chousensha.github.io
Chousensha.github.io
Core dump overflow
Notes, tutorials and walkthroughs from my path of information security enlightenment
 Techwagyu.com
Techwagyu.com
Tech Wagyu
Tech Wagyu covers stories both breaking and in-depth including in the tech, cyber security, online entertainment and civil unrest space.
 Thireus.com
Thireus.com
https://blog.thireus.com
 Danthesalmon.com
Danthesalmon.com
Dan [the] Salmon - Dan [the] Salmon
Jun 24, 2022 UFW, Docker, and Tailscale: Lessons Learned This is a cautionary tale about something that happened to me in the past few weeks. I’m posting it because I believe a lot can be learned by professionals (and others such as me) posting their security fails and problem-solving processes....
 Chmag.in
Chmag.in
CH Magazine Home | India's first digital security magazine
TechGyan All Articles Trend of CTF’s in India January 18, 2016 By Amruttaa Pardessi Capture The Flag (CTF) is an ethical hacking competition. This contest has taken its name from an outdoor game which consists of two teams and each team has to capture... 18 Jan Firewall Hardening & Best...

 Cyberpratibha.com
Cyberpratibha.com
Cyber Pratibha | Enhance Cyber Skills
One Step Towards, Secure Cyber Word It's your turn to help to secure cyber space by enhancing your technical skills including Expertise in Linux, Wireless Security, Advanced in Kali Linux, Ethical Hacking and more Start Your Journy Work as volunteer Online Classes One to one, One to many classes make you | Cyber Pratibha


 Kennyvn.com
Kennyvn.com
Kali Linux Tutorials - Kennyvn
A blog dedicated to sharing actionable Kali Linux tutorials, guides, cheatsheets, and tips and tricks.
 Hashes.com
Hashes.com
Decrypt MD5, SHA1, MySQL, NTLM, SHA256, SHA512, Wordpress, Bcrypt hashes for free online
Decrypt and crack your MD5, SHA1, SHA256, MySQL, and NTLM hashes for free online. We also support Bcrypt, SHA512, Wordpress and many more.
Technologies Used by cryptokait.com
Dns Records of cryptokait.com
A Record: 192.0.78.24 192.0.78.25AAAA Record:
CNAME Record:
NS Record: ns3.wordpress.com ns1.wordpress.com ns2.wordpress.com
SOA Record: hostmaster.wordpress.com
MX Record:
SRV Record:
TXT Record:
DNSKEY Record:
CAA Record:
Whois Detail of cryptokait.com
Domain Name: cryptokait.comRegistry Domain ID: 2436582932_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.sawbuck.com
Registrar URL: http://www.automattic.com/
Updated Date: 2021-08-25T13:10:11Z
Creation Date: 2019-09-24T00:07:41Z
Registrar Registration Expiration Date: 2022-09-24T00:07:41Z
Registrar: Automattic Inc.
Registrar IANA ID: 1531
Registrar Abuse Contact Email: [email protected]
Registrar Abuse Contact Phone: +1.8772733049
Domain Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited
Registry Registrant ID: Not Available From Registry
Registrant Name: Private Whois
Registrant Organization: Knock Knock WHOIS Not There, LLC
Registrant Street: 9450 SW Gemini Dr #63259
Registrant City: Beaverton
Registrant State/Province:
Registrant Postal Code: 97008-7105
Registrant Country: US
Registrant Phone: +1.8772738550
Registrant Phone Ext:
Registrant Fax:
Registrant Fax Ext:
Registrant Email: [email protected]
Registry Admin ID: Not Available From Registry
Admin Name: Private Whois
Admin Organization: Knock Knock WHOIS Not There, LLC
Admin Street: 9450 SW Gemini Dr #63259
Admin City: Beaverton
Admin State/Province:
Admin Postal Code: 97008-7105
Admin Country: US
Admin Phone: +1.8772738550
Admin Phone Ext:
Admin Fax:
Admin Fax Ext:
Admin Email: [email protected]
Registry Tech ID: Not Available From Registry
Tech Name: Private Whois
Tech Organization: Knock Knock WHOIS Not There, LLC
Tech Street: 9450 SW Gemini Dr #63259
Tech City: Beaverton
Tech State/Province:
Tech Postal Code: 97008-7105
Tech Country: US
Tech Phone: +1.8772738550
Tech Phone Ext:
Tech Fax:
Tech Fax Ext:
Tech Email: [email protected]
Registry Billing ID: Not Available From Registry
Billing Name: Private Whois
Billing Organization: Knock Knock WHOIS Not There, LLC
Billing Street: 9450 SW Gemini Dr #63259
Billing City: Beaverton
Billing State/Province:
Billing Postal Code: 97008-7105
Billing Country: US
Billing Phone: +1.8772738550
Billing Phone Ext:
Billing Fax:
Billing Fax Ext:
Billing Email: [email protected]
Name Server: ns1.wordpress.com
Name Server: ns2.wordpress.com
Name Server: ns3.wordpress.com
DNSSEC: unsigned
Whoisprivacy: 5
URL of the ICANN WHOIS Data Problem Reporting System: https://wdprs.internic.net/
>>> Last update of WHOIS database: 2022-06-16T01:33:01Z <<<
For more information on Whois status codes, please visit https://www.icann.org/epp
To contact the registered registrant please proceed to:
https://www.domain-contact.org
Please register your domains at; http://www.automattic.com/
This data is provided by Automattic Inc.
for information purposes, and to assist persons obtaining information
about or related to domain name registration records.
Automattic Inc. does not guarantee its accuracy.
By submitting a WHOIS query, you agree that you will use this data
only for lawful purposes and that, under no circumstances, you will
use this data to
1) allow, enable, or otherwise support the transmission of mass
unsolicited, commercial advertising or solicitations via E-mail
(spam) or
2) enable high volume, automated, electronic processes that apply
to this WHOIS server.
These terms may be changed without prior notice.
By submitting this query, you agree to abide by this policy.
 198.185.159.144
198.185.159.144
 United States
United States
 Valid SSL
Valid SSL