Privileged Access Management (PAM) Solutions | Software
One of the most full-featured privileged access management (PAM) solutions available is easy to use, well adopted and affordable. Free trial.

Stats
Alexa Rank:
Popular in Country:
Country Alexa Rank:
language: en-US
Response Time: 0.068745
SSL: Enable
Status: up
Code To Txt Ratio
Word Count 1055
Links
ratio 7.4606854372651
SSL Details
SSL Issuer:
Issuer: Amazon
Valid From: 2021-11-18 00:00:00
Expiration Date: 2022-12-16 23:59:59
SSL Organization:
Signature 0d1204d18836171aadd3902b95d4af0928508ea6
Algorithm: RSA-SHA256
Found 77 Top Alternative to Thycotic.com

 Cyberark.com
Cyberark.com
Identity Security and Access Management Leader | CyberArk
Get the most complete Identity Security and Access Management Solutions that enable secure access across any device, anywhere, at just the right time.

 Beyondtrust.com
Beyondtrust.com
Privileged Access Management, Cyber Security, and Remote Access (formerly Bomgar) | BeyondTrust
Unwanted remote access, stolen credentials, and misused privileges threaten every organization. BeyondTrust offers the industry’s broadest set of privileged access management capabilities to defend against cyber attacks. Our Privileged Access Management platform provides visibility and control over all privileged accounts, users, and access. Trusted by more than 20,000 companies and counting.
 Passwordsgenerator.net
Passwordsgenerator.net
Strong Random Password Generator
Strong Password Generator to create secure passwords that are impossible to crack on your device without sending them across the Internet, and learn over 40 tricks to keep your passwords, accounts and documents safe.
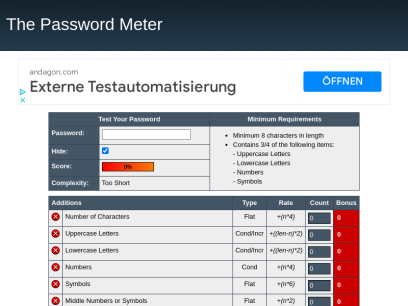
 Passwordmeter.com
Passwordmeter.com
Password Strength Checker
Additions Type Rate Count Bonus Number of Characters Flat +(n*4) Uppercase Letters Cond/Incr +((len-n)*2) Lowercase Letters Cond/Incr +((len-n)*2) Numbers Cond +(n*4) Symbols Flat +(n*6) Middle Numbers or Symbols Flat +(n*2) Requirements...

 Howsecureismypassword.net
Howsecureismypassword.net
How Secure Is My Password?
How long it would take a computer to crack your password?
 Roboform.com
Roboform.com
RoboForm Password Manager: Say Goodbye to Writing Down Passwords
Multi-platform secure password manager. One click logins on Chrome, Firefox, Safari, IE, Opera, Edge, Windows, Mac, iOS, Android.

 My1login.com
My1login.com
Identity & Access Management Solutions for Enterprise
Provide secure identity and access management and single sign-on to all applications from any device
 Dashlane.com
Dashlane.com
Password Manager App for Home, Mobile, Business | Dashlane
Live a safer life online with Dashlane password manager: Store and fill in all your passwords, personal information, and payments.

 Nordpass.com
Nordpass.com
Securely Store, Manage & Autofill Passwords | NordPass
NordPass password manager remembers complex passwords, auto-fills logins and online forms and lets you access it all from anywhere. Even when you’re offline.

 Bitwarden.com
Bitwarden.com
Bitwarden Open Source Password Manager | Bitwarden
Bitwarden is an integrated open source password management solution for individuals, teams, and business organizations

 Pleasantsolutions.com
Pleasantsolutions.com
Pleasant Solutions
Sheetcast Pleasant Password Server Paranoid (Privacy) Software Development Services Pleasant Payments Other ▾ Pleasant Contract Server JIRA Consulting Pleasant Studios Internet of Things Consumer Electronics Department Graphic Design About ▾ About Pleasant Careers
 Xkpasswd.net
Xkpasswd.net
XKPasswd - Secure Memorable Passwords
Words: Dictionary: English Number of Words: 2 3 4 5 6 7 8 9 10 Minimum Length: 4 5 6 7 8 9 10 11 12 Maximum Length: 4 5 6 7 8 9 10 11 12 Transformations: Case Transformation: -none- alternating WORD case Capitalise First Letter cAPITALISE eVERY lETTER...

 Keepersecurity.com
Keepersecurity.com
Password & Secrets Management | Keeper Security
Keeper is the top-rated password and secrets manager for protecting businesses and families from cyberthreats. Try free now!
 Keepass.info
Keepass.info
KeePass Password Safe
KeePass is a free open source password manager. Passwords can be stored in an encrypted database, which can be unlocked with one master key.
 Strongpasswordgenerator.com
Strongpasswordgenerator.com
StrongPasswordGenerator (Get a Safe Password Now) - Privacy Canada
Generate a random password! You can choose between 4 and 32 characters, and include numbers, symbols, uppercase, and lowercase letters.

 Specopssoft.com
Specopssoft.com
Specops Software - Password Security Tools for Active Directory
Specops Software develops solutions that help businesses manage password policies, secure authentication, & align with industry compliance standards.
 1password.com
1password.com
Password Manager for Families, Businesses, Teams | 1Password
A password manager, digital vault, form filler and secure digital wallet. 1Password remembers all your passwords for you to help keep account information safe.

 Centrify.com
Centrify.com
Leader in Zero Trust and Privileged Access Management (PAM) | Centrify
Zero Trust and Privileged Access Management (PAM) approach to cyber attacks minimizes your attack surface. Our services include Privileged Access, Authentication, Privilege Elevation, Audit and Monitoring.
 Dinopass.com
Dinopass.com
DinoPass - Simple password generator for kids
Password generator for creating simple, memorable and kid-friendy passwords
 Remotedesktopmanager.com
Remotedesktopmanager.com
Remote Desktop Manager - Remote Connection Management
Centralize, manage and secure access to remote connections. Remote Desktop Manager is your single pane of glass for all your remote connections.

 Devolutions.net
Devolutions.net
Remote Access and Password Management - Devolutions
Devolutions is a leading provider of remote access and enterprise password management solutions for IT professionals and business users.
 Thebitmill.com
Thebitmill.com
The Bitmill Inc. -- Security Software and Consulting
Internet security, system security, network architecture, systems consulting and custom programming.

 Netwrix.com
Netwrix.com
Netwrix | Powerful Data Security Made Easy.
Easily identify sensitive, regulated and mission-critical information in your data stores and focus on the information that truly requires protection.
 Generate-password.com
Generate-password.com
Password Generator - Generate random & secure passwords online
Automatically generated and secure passwords for social media, websites and email-accounts. Get your password quick and easy!

 Stealthbits.com
Stealthbits.com
Data Access Governance | Active Directory Security | Privileged Access Management | Stealthbits
Stealthbits protects credentials and data from insider threats, audits changes, and automates tasks for security and compliance across your infrastructure.

 Coresecurity.com
Coresecurity.com
Core Security | Cyber Threat Prevention & Identity Governance
Contact Us Support All HelpSystems Products FREE TRIALS Contact Us Support All HelpSystems Products FREE TRIALS Cyber Threat Toggle Dropdown Products Core Impact Penetration testing software Cobalt Strike Red team software Event Manager Security information and event management Network Insight Network Traffic Analysis Powertech Antivirus Server-level virus protection Security Auditor...

 Qualys.com
Qualys.com
Information Security and Compliance | Qualys
Qualys, Inc. helps your business automate the full spectrum of auditing, compliance and protection of your IT systems and web applications.

 Cisecurity.org
Cisecurity.org
CIS Center for Internet Security
CIS is a forward-thinking nonprofit that harnesses the power of a global IT community to safeguard public and private organizations against cyber threats.
 Bankinfosecurity.com
Bankinfosecurity.com
Bank information security news, training, education - BankInfoSecurity
BankInfoSecurity.com is your source for banking information security related content, including fraud, ID theft, risk management, emerging technology (authentication, cloud computing, mobile banking, social media), as well as the latest regulations and anlysis on current topics.

 Lepide.com
Lepide.com
Lepide | Detect Insider Threats and Prevent Data Breaches
Modernize your cybersecurity with our complete data security solution for enterprises looking to detect insider threats, prevent data breaches and meet compliance.

 Stickypassword.com
Stickypassword.com
Best password manager and free password safe | Sticky Password
Stop forgetting passwords now. With our free password manager, you can log in securely, autofill forms in a second, and use your passwords wherever you go.
 Csoonline.com
Csoonline.com
CSO - CSO Online – IT-Security-News für Profis
News und Insights zur Cybersicherheit im Unternehmen. Alles was CSOs wissen müssen.
 Securitymagazine.com
Securitymagazine.com
Security Magazine | The business magazine for security executives
Security provides security industry news and trends on video surveillance, cyber security, physical security, security guards, risk management, access control and more for security executives and the security industry.

 Bomgar.com
Bomgar.com
Privileged Access Management, Cyber Security, and Remote Access (formerly Bomgar) | BeyondTrust
Unwanted remote access, stolen credentials, and misused privileges threaten every organization. BeyondTrust offers the industry’s broadest set of privileged access management capabilities to defend against cyber attacks. Our Privileged Access Management platform provides visibility and control over all privileged accounts, users, and access. Trusted by more than 20,000 companies and counting.
 Solutionsreview.com
Solutionsreview.com
Solutions Review Technology News and Vendor Reviews - The Best Enterprise Technology News, and Vendor Reviews
Solutions Review - Enterprise Technology News, Vendors and Best Practices

 Jumpcloud.com
Jumpcloud.com
JumpCloud: SSO and Active Directory Reimagined
JumpCloud's revolutionary directory unifies device and identity on Windows, Mac, and Linux with cloud based SSO, MDM, MFA, PAM, and more.

 Firecompass.com
Firecompass.com
FireCompass | Continuous Automated Red Teaming | Attack Surface Management
FireCompass Continuous Automated Red Teaming (CART) and Attack Surface Management (ASM) - SaaS Platform for continuous attack surface discovery & testing.
 Heimdalsecurity.com
Heimdalsecurity.com
Heimdal Security - Proactive Cyber Security Software
Heimdal™ combines threat prevention, patch management, access management, antivirus and e-mail security into a single platform that simplifies IT operations.
 Digitalguardian.com
Digitalguardian.com
Enterprise IP & DLP Software | Digital Guardian
The Industry’s Only SaaS Solution for Enterprise DLP powered by Our unique approach to DLP allows for quick deployment and on-demand scalability, while providing full data visibility and no-compromise protection SCHEDULE A DEMO Compatible with No-Compromise Data Protection That Stops Data Loss Cloud-Delivered Powered by AWS, Digital Guardian delivers simplified...

 Online-domain-tools.com
Online-domain-tools.com
Online Domain Tools - Useful tools to make your life easier
Online Domain Tools makes your online life easier and happier. Domain tools, network tools, web and browser tools, security and privacy tools, etc.
 Darkreading.com
Darkreading.com
Dark Reading | Security | Protect The Business
Cyber security's comprehensive news site is now an online community for security professionals, outlining cyber threats and the technologies for defending against them.

 Manageengine.com
Manageengine.com
ManageEngine - IT Operations and Service Management Software
ManageEngine offers enterprise IT management software for your service management, operations management, Active Directory and security needs. Download free trial now.
 Manytools.org
Manytools.org
Your online toolshed: many tools for web developers, system admins & webworkers (a.o. Network configuration, Image conversion, String manipulation, etc)
Many tools for web developers, system admins & webworkers (a constantly growing online toolbox for: Network configuration, Image conversion, String manipulation, etc); suggest your own!

 Grc.com
Grc.com
Home of Gibson Research Corporation
Steve Gibson's and Gibson Research Corporation's Web homepage.
 Strongpasswordgenerator.org
Strongpasswordgenerator.org
Strong Password Generator
Use the Strong Password Generator to create highly secure passwords that are difficult to crack or guess. Just select the criteria for the passwords you need and copy and paste. Generate More tools at our geek tools site Bookmark this page Import password from another device Include Alpha Upper (A-Z):...
 Enpass.io
Enpass.io
Enpass: Password Manager for iOS, Android, Linux, Windows, Mac
Offline Password Manager and Secure Vault. Saves and fill in all your passwords, cards and other details. Available for Android, iOS, Mac, Windows and Linux.
 Passwordboss.com
Passwordboss.com
Password Boss | Password Management | Password Boss
Password Boss is a complete end-to-end, multi-tenant password management solution for MSPs that securely stores your business's and clients' passwords.

 Barkly.com
Barkly.com
Extended Endpoint Protection - Alert Logic
Protect sensitive data against multiple attacks with extended endpoint security protection. Alert Logic lets you monitor and isolate endpoint attacks early!
 Commonkey.com
Commonkey.com
CommonKey | Team Password Manager
CommonKey is your team password manager that increases productivity and security, helping manage all your cloud apps with a click of a button.
 Howsmyssl.com
Howsmyssl.com
How's My SSL?
Your SSL client is Probably Okay. Check out the sections below for information about the SSL/TLS client you used to render this page. Yeah, we really mean "TLS", not "SSL". Version Good Your client is using TLS 1.3, the most modern version of the encryption protocol. It gives you access...

 Adsecurity.org
Adsecurity.org
Active Directory Security – Active Directory & Enterprise Security, Methods to Secure Active Directory, Attack Methods & Effective Defenses, PowerShell, Tech Notes, & Geek Trivia…
May 27 2020 From Azure AD to Active Directory (via Azure) – An Unanticipated Attack Path By Sean Metcalf in Cloud Security, Microsoft Security, TheCloud For most of 2019, I was digging into Office 365 and Azure AD and looking at features as part of the development of the new...

 Ekransystem.com
Ekransystem.com
Ekran System - Insider Threat Protection Software
Ekran System - software to monitor privileged users and audit employee activity, detect insider threats, and protect servers in real time. Try a free demo now!
 Doubleoctopus.com
Doubleoctopus.com
Double Octopus | The Leader in Workforce Passwordless MFA
Provider of industry-leading FIDO-certified, rotation-based passwordless MFA with the fullest support for enterprise complexity. Click here for more!

 Passbolt.com
Passbolt.com
Passbolt | The open source password manager for teams
Passbolt is an open source password manager designed for team collaboration. Securely generate, store, manage and monitor your team credentials. Try it now!
Technologies Used by thycotic.com
Dns Records of thycotic.com
A Record: 18.65.39.129 18.65.39.69 18.65.39.115 18.65.39.20AAAA Record: 2600:9000:21c7:ca00:18:542f:9900:93a1 2600:9000:21c7:400:18:542f:9900:93a1 2600:9000:21c7:9600:18:542f:9900:93a1 2600:9000:21c7:1a00:18:542f:9900:93a1 2600:9000:21c7:800:18:542f:9900:93a1 2600:9000:21c7:2000:18:542f:9900:93a1 2600:9000:21c7:2600:18:542f:9900:93a1 2600:9000:21c7:a000:18:542f:9900:93a1
CNAME Record:
NS Record: ns-644.awsdns-16.net ns-459.awsdns-57.com ns-1778.awsdns-30.co.uk ns-1230.awsdns-25.org
SOA Record: awsdns-hostmaster.amazon.com
MX Record: thycotic-com.mail.protection.outlook.com
SRV Record:
TXT Record: intacct-esk=4FED1A5020FAD94FE053ED06A8C0E14D google-site-verification=GjMbd_jDVcIDKxEF67SVKpov6bbC3QL67MzIXNuqwN4 google-site-verification=5ETo3ixMHGrpDDIygAV4DAg_wPm6LlLD1KCod2gMmgs globalsign-domain-verification=f0cfd1b2ff8cea89120b7ebe87c4a6ce globalsign-domain-verification=c21d746f494e6dab4e9a732dd9296c7a globalsign-domain-verification=7463fb52ab0de24d293ac90791a2575f g8rhh6v81pn5c9pg7b8jcgb7go bao107t7ee1u4baot9nf7gec5j atlassian-domain-verification=s8SNnNaOlQMHbTLBqVI3aLQDUQibX7iBF3Cl2QP1wuX1G+UI807yV-9WvDzB8KcN atlassian-domain-verification=oYUbX245yzALBSugbORgFSzQ15GaA73RTNGyafVeTL5Y8eLTSTllNQ5t3apxVGAx apple-domain-verification=8Rxj47jSffVSUE7P _globalsign-domain-verification=kOEs5YF-4pCpxMqD0zxvyjuHy5AevZCQ20iIJLAKzV OSSRH-50288 v=spf1 include:spf1.thycotic.com include:spf2.thycotic.com include:et._spf.pardot.com ip4:192.174.81.234 ip4:192.174.90.242 -all smartsheet-site-validation=qUbzgwojNjpEV6bBaBGR65O68M2bk7vD site24x7-signals-domain-verification=556c74dae0bfe396f2e1d13d229fc98c pardot_101722_*=42ff07edb1890f3a170b787bf92427adb2c14d2e4b392b829a4a6bc0927ed249 logmein-verification-code=8122af67-e69f-458e-9f11-6fc0dbe1e30b
DNSKEY Record:
CAA Record: sectigo.com letsencrypt.org godaddy.com globalsign.com digicert.com amazon.com
Whois Detail of thycotic.com
Domain Name: THYCOTIC.COMRegistry Domain ID: 379763_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.godaddy.com
Registrar URL: http://www.godaddy.com
Updated Date: 2019-06-17T22:10:01Z
Creation Date: 1997-07-26T04:00:00Z
Registry Expiry Date: 2027-07-25T04:00:00Z
Registrar: GoDaddy.com, LLC
Registrar IANA ID: 146
Registrar Abuse Contact Email: [email protected]
Registrar Abuse Contact Phone: 480-624-2505
Domain Status: clientDeleteProhibited https://icann.org/epp#clientDeleteProhibited
Domain Status: clientRenewProhibited https://icann.org/epp#clientRenewProhibited
Domain Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited
Domain Status: clientUpdateProhibited https://icann.org/epp#clientUpdateProhibited
Name Server: NS-1230.AWSDNS-25.ORG
Name Server: NS-1778.AWSDNS-30.CO.UK
Name Server: NS-459.AWSDNS-57.COM
Name Server: NS-644.AWSDNS-16.NET
DNSSEC: unsigned
URL of the ICANN Whois Inaccuracy Complaint Form: https://www.icann.org/wicf/
>>> Last update of whois database: 2022-07-23T10:16:50Z <<<
For more information on Whois status codes, please visit https://icann.org/epp
NOTICE: The expiration date displayed in this record is the date the
registrar's sponsorship of the domain name registration in the registry is
currently set to expire. This date does not necessarily reflect the expiration
date of the domain name registrant's agreement with the sponsoring
registrar. Users may consult the sponsoring registrar's Whois database to
view the registrar's reported date of expiration for this registration.
TERMS OF USE: You are not authorized to access or query our Whois
database through the use of electronic processes that are high-volume and
automated except as reasonably necessary to register domain names or
modify existing registrations; the Data in VeriSign Global Registry
Services' ("VeriSign") Whois database is provided by VeriSign for
information purposes only, and to assist persons in obtaining information
about or related to a domain name registration record. VeriSign does not
guarantee its accuracy. By submitting a Whois query, you agree to abide
by the following terms of use: You agree that you may use this Data only
for lawful purposes and that under no circumstances will you use this Data
to: (1) allow, enable, or otherwise support the transmission of mass
unsolicited, commercial advertising or solicitations via e-mail, telephone,
or facsimile; or (2) enable high volume, automated, electronic processes
that apply to VeriSign (or its computer systems). The compilation,
repackaging, dissemination or other use of this Data is expressly
prohibited without the prior written consent of VeriSign. You agree not to
use electronic processes that are automated and high-volume to access or
query the Whois database except as reasonably necessary to register
domain names or modify existing registrations. VeriSign reserves the right
to restrict your access to the Whois database in its sole discretion to ensure
operational stability. VeriSign may restrict or terminate your access to the
Whois database for failure to abide by these terms of use. VeriSign
reserves the right to modify these terms at any time.
The Registry database contains ONLY .COM, .NET, .EDU domains and
Registrars.
 104.17.193.105
104.17.193.105

 InValid
SSL
InValid
SSL