Leader in Cyber Security Solutions | Check Point Software
Check Point Infinity architecture delivers consolidated Gen V cyber security across networks, cloud, and mobile environments.

Stats
Alexa Rank:
Popular in Country:
Country Alexa Rank:
language: en-US
Response Time: 0.120157
SSL: Enable
Status: up
Code To Txt Ratio
Word Count 461
Links
ratio 9.9391985833754
SSL Details
SSL Issuer:
Issuer: Go Daddy Secure Certificate Authority - G2
Valid From: 2021-10-30 07:12:47
Expiration Date: 2022-10-28 18:15:21
SSL Organization:
Signature 55d22c88a9faf66fae46a3ba038fd831d47f0bd0
Algorithm: RSA-SHA256
Found 77 Top Alternative to Checkpoint.com

 Paloaltonetworks.com
Paloaltonetworks.com
Global Cybersecurity Leader - Palo Alto Networks
Palo Alto Networks enables your team to prevent successful cyberattacks with an automated approach that delivers consistent security across cloud, network and mobile.
 Fortinet.com
Fortinet.com
Global Leader of Cyber Security Solutions and Services | Fortinet
Fortinet delivers award-winning cyber security solutions across the entire digital attack surface, securing devices, data, and applications from the data center to the cloud to the home office.
 Juniper.net
Juniper.net
Juniper Networks – Leader in AI Networking, Cloud, & Connected Security Solutions
Juniper Networks dramatically simplifies network operations and driving super experiences for end users. Our solutions deliver industry-leading insight, automation, security and AI to drive real business results. We believe that powering connections will bring us closer together while empowering us to solve the world’s greatest challenges.
 Forcepoint.com
Forcepoint.com
Forcepoint | Security Simplified
Forcepoint ONE is security simplified. Get consistent security across any app, device or location and control it from one platform.

 F5.com
F5.com
F5 | Multi-Cloud Security and Application Delivery
F5 application services ensure that applications are always secure and perform the way they should—in any environment and on any device.
 Csoonline.com
Csoonline.com
CSO - CSO Online – IT-Security-News für Profis
News und Insights zur Cybersicherheit im Unternehmen. Alles was CSOs wissen müssen.

 Sonicwall.com
Sonicwall.com
Next-Gen Firewalls & Cybersecurity Solutions - SonicWall
Defend SMBs, enterprises and governments from advanced cyber attacks with SonicWall's award-winning firewalls and cyber security solutions.

 Barracuda.com
Barracuda.com
Barracuda Networks
Barracuda Networks is the worldwide leader in Security, Application Delivery and Data Protection Solutions.
 Imperva.com
Imperva.com
Cyber Security Leader | Imperva, Inc.
Imperva provides complete cyber security by protecting what really matters most—your data and applications—whether on-premises or in the cloud.

 Sans.org
Sans.org
Cyber Security Training | SANS Courses, Certifications & Research
SANS Institute is the most trusted resource for cybersecurity training, certifications and research. Offering more than 60 courses across all practice areas, SANS trains over 40,000 cybersecurity professionals annually.

 Rapid7.com
Rapid7.com
Cybersecurity & Compliance Solutions & Services | Rapid7
Supercharge your security impact with Rapid7, delivering shared visibility, analytics, and automation to unite security, IT, and DevOps teams.

 Threatpost.com
Threatpost.com
Threatpost | The first stop for security news
Threatpost, is an independent news site which is a leading source of information about IT and business security for hundreds of thousands of professionals worldwide.
 Cisco.com
Cisco.com
Cisco - Networking, Cloud, and Cybersecurity Solutions
Cisco delivers innovative software-defined networking, cloud, and security solutions to help transform your business, empowering an inclusive future for all.

 Mitre.org
Mitre.org
The MITRE Corporation
About Corporate Overview Our History Mission and Values Visiting MITRE Leadership Executive Team Board of Trustees Fellows Technical Fellows Visiting Fellows Awards and Recognition Corporate Social Responsibility Building a Foundation for the Future MITRE Staff Cultivates Los Angeles' Science Ecosystem Bringing Real World STEM to Students Building Partnerships and Diversity,...

 Fortiguard.com
Fortiguard.com
FortiGuard
View by Product Network Intrusion Protection Anti-Recon and Anti-Exploit Secure DNS IP Reputation/Anti-Botnet Indicators of Compromise IP Geolocation Service Cloud Workload Security Service Content and Endpoint Endpoint Detection & Response Anti-Virus Endpoint Vulnerability Device Detection ANN and NDR Sandbox Behavior Engine Application Web Filtering Anti-Spam Application Control Industrial Security Services...

 Trendmicro.com
Trendmicro.com
#1 bei Cloud-Sicherheit & Endpunkt-Cybersicherheit | Trend Micro (DE)
Trend Micro ist der weltweit führende Anbieter von Plattformlösungen für Cloud-Sicherheit, XDR und Cybersicherheit – für Unternehmen, Rechenzentren, Cloud-Umgebungen, Netzwerke und Endpunkte.
 Meraki.com
Meraki.com
Wi-Fi 6E | Network Security | Switches | Routers | Cisco Meraki
Cisco Meraki is the leader in cloud controlled Wi-Fi, routing, and security. Secure and scalable, learn how Cisco Meraki enterprise networks simply work.
 Arubanetworks.com
Arubanetworks.com
Aruba | Enterprise Networking and Security Solutions
Aruba is the industry leader in wired, wireless and security networking solutions for todays experience edge.

 Broadcom.com
Broadcom.com
Broadcom Inc. | Connecting Everything
Broadcom Inc. is a global technology leader that designs, develops and supplies semiconductor and infrastructure software solutions.

 Esecurityplanet.com
Esecurityplanet.com
eSecurity Planet: Latest Cybersecurity News for IT Professionals
eSecurity Planet provides the latest cybersecurity news, trends, and software reviews for IT leaders. Browse our buyer's guides and analysis now.
 Tenable.com
Tenable.com
Tenable® - The Cyber Exposure Company
Welcome to the modern era of cyber exposure. Join the movement.

 Portswigger.net
Portswigger.net
Web Application Security, Testing, & Scanning - PortSwigger
PortSwigger offers tools for web application security, testing, & scanning. Choose from a range of security tools, & identify the very latest vulnerabilities.

 Radware.com
Radware.com
ShieldSquare Captcha
We apologize for the inconvenience... ...but your activity and behavior on this site made us think that you are a bot. Note: A number of things could be going on here. If you are attempting to access this site using an anonymous Private/Proxy network, please disable that and try accessing...

 Crowdstrike.com
Crowdstrike.com
CrowdStrike: Stop breaches. Drive business.
CrowdStrike is a global cybersecurity leader with an advanced cloud-native platform for protecting endpoints, cloud workloads, identities and data.
 Darkreading.com
Darkreading.com
Dark Reading | Security | Protect The Business
Cyber security's comprehensive news site is now an online community for security professionals, outlining cyber threats and the technologies for defending against them.
 Securityweek.com
Securityweek.com
Cybersecurity News, Insights and Analysis | SecurityWeek
SecurityWeek provides cybersecurity news and information to global enterprises, with expert insights and analysis for IT security professionals.
 Citrix.com
Citrix.com
All in one Workspace Solution for Secure Access to Apps and Data - Citrix
Citrix workspace software delivers the business technology that creates a simple, secure and better way to work from anywhere and on any device.

 Networklessons.com
Networklessons.com
NetworkLessons.com - Networking in Plain English
NetworkLessons.com teaches you everything about Cisco R&S, Security, Wireless and Linux. Great Courses, Lessons and Learning Material.
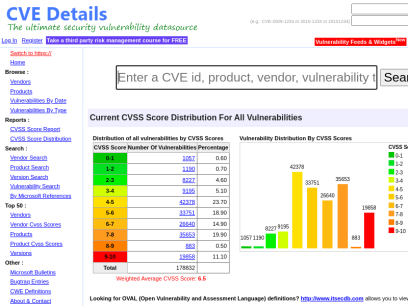
 Cvedetails.com
Cvedetails.com
CVE security vulnerability database. Security vulnerabilities, exploits, references and more
CVEdetails.com is a free CVE security vulnerability database/information source. You can view CVE vulnerability details, exploits, references, metasploit modules, full list of vulnerable products and cvss score reports and vulnerability trends over time
 Netgate.com
Netgate.com
Netgate
Netgate is an open-source driven secure networking company that provides appliance and software-based firewall, VPN and routing solutions including pfSense

 Checkfirewalls.com
Checkfirewalls.com
Check Point Security Appliances & Security Gateways | CheckFirewalls.com
Check Point Products, Consulting and Information Check Point - A Leader in Securing the Internet Previous Next Infinity Vision ThreatCloud translates threat intelligence data from hundreds of millions of sensors worldwide into proactive security protections across the Infinity architecture. Check Point Infinity Vision Infinity-Vision is the unified management platform for...

 Infosecinstitute.com
Infosecinstitute.com
IT & Security Education, Certifications, Awareness & Phishing Simulator - Infosec
Infosec helps IT and security professionals advance their careers with skills development and certifications while empowering all employees with security awareness and privacy training to stay cyber-safe at work and home.

 Watchguard.com
Watchguard.com
WatchGuard Technologies | Network Security, Secure Wi-Fi, MFA, and Endpoint Security Solutions
Award-winning solutions that are easy to deploy and manage, making enterprise-grade security accessible to any organization regardless of size or expertise.
 Comodo.com
Comodo.com
Cybersecurity Breaches Stop Here | Comodo Cybersecurity
Comodo Breach detection identifies active advanced threats operating inside a network. Understand the importance of choosing Comodo's Threat Protection.
 Scmagazine.com
Scmagazine.com
SC Media | Homepage
The latest in-depth, unbiased news, analysis and perspective to keep cybersecurity professionals informed, educated and enlightened about the market.

 Ciscopress.com
Ciscopress.com
Cisco Press: Source for Cisco Technology, CCNA, CCNP, CCIE Self-Study | Cisco Press
Cisco Press is part of a recommended learning path from Cisco Systems that combines instructor-led training with hands-on instruction, e-learning, & self-study.

 Owasp.org
Owasp.org
OWASP Foundation | Open Source Foundation for Application Security
OWASP Foundation, the Open Source Foundation for Application Security on the main website for The OWASP Foundation. OWASP is a nonprofit foundation that works to improve the security of software.
 Mcafee.com
Mcafee.com
Antivirus, VPN, Identity & Privacy Protection | McAfee
McAfee award-winning Antivirus and VPN, now includes Identity & Privacy Protection! Complete online protection for you and your family, available on PC, Mac, Android, or iOS. Get protection now!

 Kaspersky.com
Kaspersky.com
Kaspersky-Cybersicherheitslösungen für Privatanwender und Unternehmen | Kaspersky
Kaspersky bietet unterschiedliche Schutzniveaus für Ihre privaten Geräte und hält sie so frei von Viren und Online-Bedrohungen. Erfahren Sie hier, was am besten zu Ihnen passt

 Acunetix.com
Acunetix.com
Acunetix | Web Application Security Scanner
Acunetix is an end-to-end web security scanner that offers a 360 view of an organization’s security. Allowing you to take control of the security of all you web applications, web services, and APIs to ensure long-term protection. Acunetix’s scanning engine is globally known and trusted for its unbeatable speed and precision.

 Indeni.com
Indeni.com
Security Infrastructure Automation | Locates Issues Automatically
Security Infrastructure Automation - visibility your team needs to see where issues may happen + filter to know which ones matter + specific steps to fix them.

 Symantec.com
Symantec.com
Symantec Enterprise Cloud
To meet today's Cyber Security challenges, enterprises need an integrated cyber defense platform that integrates industry-leading solutions and solves for the most pressing C-level challenges like evolving threats, privacy & compliance, and digital transformation.

 Websense.com
Websense.com
Forcepoint | Security Simplified
Forcepoint ONE is security simplified. Get consistent security across any app, device or location and control it from one platform.

 Alienvault.com
Alienvault.com
AlienVault is now AT&T Cybersecurity
At AT&T Cybersecurity our mission is to provide phenomenal threat intelligence, collaborative defense & effective security for organizations of all sizes.
 Arista.com
Arista.com
Data-Driven Cloud Networking - Arista
Arista Networks was founded to pioneer and deliver software-driven cloud networking solutions for large data center storage and computing environments. Arista’s award-winning platforms, ranging in Ethernet speeds from 10 to 100 gigabits per second,

 Duo.com
Duo.com
Two-Factor Authentication & Data Protection | Duo Security
Protect your workforce and user data from cybersecurity risks with Duo’s Multifactor Authentication app (Mfa), 2fa, remote access, and zero-trust solutions. Demo today.

 Ui.com
Ui.com
Ubiquiti - Simplifying IT
Technology platforms for Internet Access, Enterprise, and SmartHome applications.
 Etutorials.org
Etutorials.org
eTutorials.org
Welcome to eTutorials.org - your source for thousands online tutorials, useful tips, articles, and researched recommendations. You can surf through our collection of free online tutorials. Just choose the language or section you are interested in learning in the left nav, or use the site search bar at the very...

 Yurisk.info
Yurisk.info
Yuri Slobodyanyuk's blog on IT Security and Networking
Yuri Slobodyanyuk's blog on IT Security and Networking –
 Draytek.com
Draytek.com
Home | DrayTek
DrayTek Corporation is a Taiwan-based manufacturer of SMB networking equipment, including VPN Routers, managed Switches, wireless AP, and management systems.

 Mikrotik.com
Mikrotik.com
MikroTik Routers and Wireless
MikroTik makes networking hardware and software, which is used in nearly all countries of the world. Our mission is to make existing Internet technologies faster, more powerful and affordable to wider range of users.
 Extremenetworks.com
Extremenetworks.com
End-to-End Cloud Driven Networking Solutions - Extreme Networks
Extreme Networks delivers end-to-end, cloud-driven networking solutions and top-rated services and support to advance our customers' digital transformation efforts and deliver progress like never before.
 F-secure.com
F-secure.com
Produkte für Online-Sicherheit und -Datenschutz | F-Secure
F-Secure entwickelt und vertreibt mehrfach ausgezeichnete Erkennungs- & Reaktionslösungen (Detection & Response Lösungen) kombiniert mit herausragenden Cyber-Sicherheitsservices, um Unternehmen sowie Personen vor Cyberangriffen optimal zu schützen.

 Openvpn.net
Openvpn.net
Business VPN | Next-Gen VPN | OpenVPN
OpenVPN provides flexible business VPN solutions for an enterprise to secure all data communications and extend private network services while maintaining security.

 Us-cert.gov
Us-cert.gov
Homepage | CISA
As part of its mission, CISA leads the effort to enhance the security, resiliency, and reliability of the Nation's cybersecurity and communications infrastructure.

 Ietf.org
Ietf.org
IETF | Internet Engineering Task Force
Welcome to the IETF IETF Hackathon in Philadelphia Help define and improve new Internet technologies by working on running code in Philadelphia on 23-24 July. Learn more about how anyone can participate Upcoming events IETF 114 Philadelphia IETF 114 starts Saturday 23 July and runs through Friday afternoon, 29 July....

 Eset.com
Eset.com
Malware Protection & Internet Security | ESET
Europe Albania Armenia Austria Azerbaijan Belarus Belgium (Dutch) Belgium (French) Bosnia and Herzegovina Bulgaria Croatia Cyprus Czech Republic Denmark Estonia Estonia (Russian) Finland France Georgia Germany Greece Greece (English) Hungary Iceland Ireland Italy Latvia Latvia (Russian) Lithuania Luxembourg Malta Moldova Montenegro Netherlands North Macedonia Norway Poland Portugal Romania Russia Serbia...

 Norse-corp.com
Norse-corp.com
Best Internet Security Software in 2020: The Ultimate Guide
Best Internet Security Software in 2020: Protect Your Computer from Cyber Threats with these Security Systems Think about how much time we spend online. We use our computers and devices to communicate with family, friends, and coworkers. We buy things online all the time. It is getting more common just...
Technologies Used by checkpoint.com
Dns Records of checkpoint.com
A Record: 209.87.209.100AAAA Record:
CNAME Record:
NS Record: ns1.checkpoint.com ns4.checkpoint.com ns9.checkpoint.com ns2.checkpoint.com
SOA Record: system.checkpoint.com
MX Record: tls2-us.checkpoint.com tls2.checkpoint.com
SRV Record:
TXT Record: google-site-verification=dwMGbISN9laSvidELOpgLRccCPcbGc5WMQIcFdo_3Ps google-site-verification=XG4zgx5SK5nmDbaphm5tc2OTZOOQW9LWzJwOUfdqcIs j0r31jspuaai48ae3d7rab3k4e MS=ms61202101 google-site-verification=rFuYxjFBb219O8AIjD8joMkMWhtZPanxPJS-6s6lN3w 45d45d4e-f35c-4473-9360-68660dbf576d jR=TrQdaY5lxw4bR0=NDW9TrJSzVdu-9u4xaFPuF5EZV v=spf1 include:spf1.checkpoint.com include:sendgrid.net include:spf.protection.outlook.com include:stspg-customer.com include:_spf.salesforce.com include:mail.zendesk.com include:mktomail.com -all apple-domain-verification=7QhtdqjdDG2t0PMa google-site-verificationgoogle-site-verification=sTWXCIRPR57b1uy4_mUdDXOP UAh5Ux7VaeD_XxRGs6Y ivtccuvjt7kv0cnop38g5gn1ob status-page-domain-verification=2h0hq9z9ztj5 hvtq0fjm2jxf9j7kr459rm3g30dc3svl facebook-domain-verification=r4djys91aknh85fhkxmz3z5t48gt4q google-site-verification=cr-Qr8qr0FvJM7rcCIBbqlvDMj9NGS52rcUPnoRgqjs mongodb-site-verification=aCsGW9rrjprkpiRFqzJ8lnd9AooUUBNg 70fdee12-bf32-4950-92bc-91a3632bd3f6 8a2f84e6-93c4-45cf-9759-8e724f1aa616 lyIRWpl30ICYZA1WEdosDihosuS0m3ahty0WpjuUcIoVImkL60t5Kor5QyQowt29jmi8JBmQF+0AYPnbpMOUnA== 34CDDF42E93DC8291A9FFB03F2782CB4406FE5842A2FC9E75760DC7CE8988EFA 4ee983f9-5422-4889-a5ba-1df355c2973b jqh0Jx01f2FL5Ktxt+ugQQ3RS3PWtK0kXxapIgEb/9I+/r0fTaeE7oXzMQUAED9ifJ/156eRCnddwrwbjIE5QQ== atlassian-domain-verification=vGGhyBtb9giES5RLUiWdtS3IOCoMaXbH5a6/ODT5EKQj1KUvzcxI5cZlXSL8EFST 37d894f4-2dab-4879-b69a-12cae50ccfc4 7b4c4c32-2a80-48d7-ab91-dfd4cf41dfe4 google-site-verification=vPb8jQJ2tMku_eJtjkdiri8EIiepr76S2543L_mgqO0 notion_verify_]-KBzH-e+aa7ja2_MeLin9#*@McMu5rP44_*,]yU?50i~.nuQ8twrcmR=F0A8.2CCsp>s~ fbd29d20-3129-4d07-aff9-0b67547c8bdf q5upo64pn9dfl0u34h2a1bkk1f docusign=9500ab24-ae00-4143-934c-5ad0edbea319 atlassian-domain-verification=OAFLhunIHAsvjL1SCeeNaYiPslEf7JXjseLgxMXSyiKvzuqI/y3v/mfQHaFoC9uY google-site-verification=vYWPDJt28gEcEjzGCiN18Rnb-udh_2qF1puEbWPp8wI 5452fc6c472e4ce1bfb45f7f0ca753d4 bd1cea06-a5bf-4bfd-a039-9a725419cf23 36988e76-f426-444a-bf29-0f7d16d2a1a8
DNSKEY Record:
CAA Record:
Whois Detail of checkpoint.com
Domain Name: checkpoint.comRegistry Domain ID: 68307_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.domainthenet.com
Registrar URL: http://www.domainthenet.com
Update Date: 2022-03-01T10:14:00.000Z
Creation Date: 1994-03-29T05:00:00.000Z
Registrar Registration Expiration Date: 2023-03-30T04:00:00.000Z
Registrar: DomainTheNet.com
Registrar IANA ID: 10007
Registrar Abuse Contact Email: [email protected]
Registrar Abuse Contact Phone:
Reseller:
Domain Status: clientTransferProhibited https://www.icann.org/epp#clientTransferProhibited
Domain Status: clientDeleteProhibited https://www.icann.org/epp#clientRenewProhibited
Registry Registrant ID:
Registrant Name: Domain Admin
Registrant Organization: Check Point Software Technologies Ltd.
Registrant Street: 5 Hasolelim St.
Registrant City: Tel Aviv
Registrant State/Province:
Registrant Postal Code: 6789705
Registrant Country: IL
Registrant Phone: +972.36241100
Registrant Fax: +
Registrant Email: [email protected]
Registry Admin ID:
Admin Name: Domain Admin
Admin Organization: Check Point Software Technologies LTD
Admin Street: 5 Hasolelim St
Admin City: Tel Aviv
Admin State/Province:
Admin Postal Code: 67897
Admin Country: IL
Admin Phone: +972.37534555
Admin Fax: +972.36241100
Admin Email: [email protected]
Registry Tech ID:
Tech Name: Domain Admin
Tech Organization: Check Point Software Technologies LTD
Tech Street: 5 Hasolelim St
Tech City: Tel Aviv
Tech State/Province:
Tech Postal Code: 67897
Tech Country: IL
Tech Phone: +972.37534555
Tech Fax: +972.36241100
Tech Email: [email protected]
Name Server: ns2.checkpoint.com
Name Server: ns1.checkpoint.com
Name Server: ns9.checkpoint.com
Name Server: ns4.checkpoint.com
DNSSEC: unsigned
URL of the ICANN WHOIS Data Problem Reporting System: http://wdprs.internic.net/
>>> Last update of WHOIS database: 2022-07-18T00:07:17Z <<<
For more information on Whois status codes, please visit
https://www.icann.org/resources/pages/epp-status-codes-2014-06-16-en
You are not authorized to access or query our WHOIS database through
the use of high-volume, automated, electronic processes. The data in
DomainTheNet's WHOIS database (''Data'') is provided by
DomainTheNet for information purposes only. DomainTheNet
does not guarantee the accuracy of this Data and it is provided ''as-is''.
By submitting a WHOIS query, you agree that you will use this Data
only for lawful purposes and that under no circumstances will you use
this Data to: (1) allow, enable, or otherwise support the transmission
of mass unsolicited, commercial advertising or solicitations via mail,
email (spam), telephone or facsimile, or solicitations to entities
other than the data recipients own, existing customers; or (2) enable
high-volume, automated, electronic processes that apply to
DomainTheNet (or its systems). The compilation, repackaging,
dissemination, distribution or other use of this Data is expressly
prohibited without the prior written consent of DomainTheNet
You agree not to use high-volume, automated, electronic processes to
access or query the WHOIS database. DomainTheNet reserves the
right to terminate your access to the DomainTheNet WHOIS
database in its sole discretion, including without limitation, for
excessive querying of the WHOIS database or for failure to otherwise
abide by this policy.
DomainTheNet reserves the right to modify these terms at any time.
By submitting this query, you agree to abide by the terms of this policy.
 34.107.151.202
34.107.151.202
 United States
United States
 Valid SSL
Valid SSL