evilsocket
Hi, my name is Simone (a male name in my country) and on the internet I'm known as evilsocket. I like computers, music, dogs, [books](https://www.goodreads.com/evilsocket), physics, [photography and t

Stats
Alexa Rank:
Popular in Country:
Country Alexa Rank:
language: en
Response Time: 0.098166
SSL: Enable
Status: up
Code To Txt Ratio
Word Count 289
Links
ratio 19.343065693431
SSL Details
SSL Issuer:
Issuer: Cloudflare Inc ECC CA-3
Valid From: 2022-06-17 00:00:00
Expiration Date: 2023-06-17 23:59:59
SSL Organization:
Signature ee263e124a2b3b945a154de6185b255259a85daa
Algorithm: ecdsa-with-SHA256
Found 74 Top Alternative to Evilsocket.net
 Wifipineapple.com
Wifipineapple.com
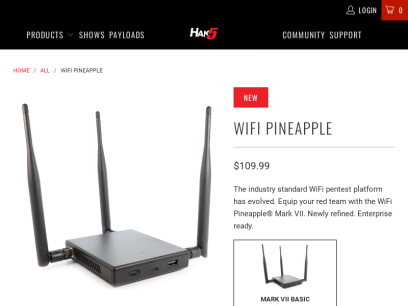
WiFi Pineapple - Hak5
The industry standard WiFi pentest platform has evolved. Equip your red team with the WiFi Pineapple® Mark VII. Newly refined. Enterprise ready.

 Bettercap.org
Bettercap.org
:: bettercap
Core events.stream ticker caplets update api.rest ui c2 Bluetooth LE WiFi HID on 2.4Ghz IPv4 / IPv6 net.recon net.probe net.sniff - net.fuzz syn.scan wake on lan Spoofers arp.spoof dns.spoof dhcp6.spoof ndp.spoof (IPv6) Proxies any.proxy packet.proxy tcp.proxy http.proxy https.proxy Servers http.server https.server mdns.server mysql.server (rogue) Utils mac.changer gps
 Hakshop.com
Hakshop.com
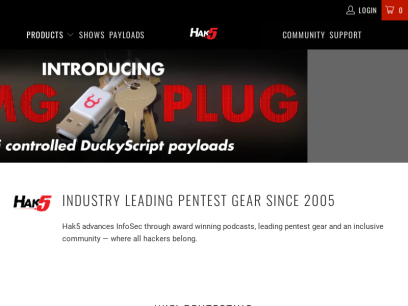
Hacking Tools & Media | Hak5 Official Site
Hak5 — industry leading hacker tools & award winning hacking shows for red teams, pentesters, cyber security students and IT professionals. Creators of the WiFi Pineapple, USB Rubber Ducky & more. Home to an inclusive information security community. Established in 2005.


 Apk-deguard.com
Apk-deguard.com
DeGuard | Statistical Deobfuscation for Android
DeGuard | Statistical Deobfuscation for Android About Contact Us Share on Facebook Share on Twitter Share on Google+ Share on LinkedIn Statistical Deobfuscation for Android DeGuard reverses the process of obfuscation performed by Android obfuscation tools. This enables numerous security analyses, including code inspection and predicting libraries. NEWS: We have...

 Fuzzing-project.org
Fuzzing-project.org
The Fuzzing Project - Background
The Fuzzing Project Fuzzing is a powerful strategy to find bugs in software. The idea is quite simple: Generate a large number of randomly malformed inputs for a software to parse and see what happens. If the program crashes then something is likely wrong. While fuzzing is a well-known strategy,...

 Pnfsoftware.com
Pnfsoftware.com
JEB Decompiler by PNF Software
PNF Software is the maker of JEB, the most powerful interactive Android app decompiler, built by and for security engineers.Decompile and debug APK files and obfuscated Dalvik bytecode. Decompile Intel x86, ARM and MIPS executable programs and malware. Reverse engineer document files. Script your automation needs and write extensions with our API.

 Charlesreid1.com
Charlesreid1.com
charlesreid1
wiki: charlesreid1.com/wiki the wiki is a compilation of reading material, notes, scripts, logs, guides, lecture notes, and scattered thoughts. gitea: git.charlesreid1.com git.charlesreid1.com is where all of my code projects are hosted. gitea is a self-hosted github clone written in go. github: @charlesreid1 follow my coding work on github....
 Secureideas.com
Secureideas.com
Secure Ideas: Professionally Evil Penetration Testing
Secure Ideas is a penetration testing firm. We strive to help our clients improve their security postures and train the next generation of professionals.
 Hak5.org
Hak5.org
Hacking Tools & Media | Hak5 Official Site
Hak5 — industry leading hacker tools & award winning hacking shows for red teams, pentesters, cyber security students and IT professionals. Creators of the WiFi Pineapple, USB Rubber Ducky & more. Home to an inclusive information security community. Established in 2005.

 Doyler.net
Doyler.net
Home
Hello hackers, Welcome to Doyler.net, Your New Home for All Things InfoSec Learn More What we do While we’re still working on courses (and services?), here’s a smattering of what you can find here at doyler.net. Learn Penetration Testing Want to learn penetration testing? Interested in protecting your organization or...
 Javadecompilers.com
Javadecompilers.com
Java decompiler online
Java decompilers online: *JAD, *JDCore, *Procyon, *Fernflower, *CFR. ✓ A user interface to extract source code from .class and .jar ‘binary’ files.
 Apkdecompilers.com
Apkdecompilers.com
Apache2 Ubuntu Default Page: It works
Ubuntu's Apache2 default configuration is different from the upstream default configuration, and split into several files optimized for interaction with Ubuntu tools. The configuration system is fully documented in /usr/share/doc/apache2/README.Debian.gz. Refer to this for the full documentation. Documentation for the web server itself can be found by accessing the manual...
 Adeptus-mechanicus.com
Adeptus-mechanicus.com
Main
"Turning and turning in the widening gyre The falcon cannot hear the falconer; Things fall apart; the centre cannot hold; Mere anarchy is loosed upon the world, The blood-dimmed tide is loosed, and everywhere The ceremony of innocence is drowned; The best lack all conviction, while the worst Are full...

 Bytecodeviewer.com
Bytecodeviewer.com
Bytecode Viewer - Java & Android APK Reverse Engineering Suite/Tool
A Java Reverse Engineering Suite. GUI Java And APK Decompiler, Editor, Debugger And More.
 Bashbunny.com
Bashbunny.com
Bash Bunny - Hak5
The groundbreaking payload platform that introduced multi-vector USB attacks has evolved.Pull off covert attacks or IT automation tasks faster than ever with just the flick of a switch. The NEW Bash Bunny Mark II goes from plug to pwn in 7 seconds — so when the light turns green it's a hacked machine.Now with faster pe

 Wordpress.com
Wordpress.com
WordPress.com: Fast, Secure Managed WordPress Hosting
Create a free website or build a blog with ease on WordPress.com. Dozens of free, customizable, mobile-ready designs and themes. Free hosting and support.
 Androguard.readthedocs.io
Androguard.readthedocs.io
Welcome to Androguard’s documentation! — Androguard 3.4.0 documentation
Welcome to Androguard’s documentation!¶ Androguard is a full python tool to play with Android files. It is designed to work with Python 3 only. DEX, ODEX APK Android’s binary xml Android resources Disassemble DEX/ODEX bytecodes Decompiler for DEX/ODEX files You can either use the cli or graphical frontend for androguard,...
 Cooltrickshome.blogspot.com
Cooltrickshome.blogspot.com
Advance Programs and Tricks in Java
A blog about all the Advanced Programs and Tricks I learned...
 Brightdevelopers.com
Brightdevelopers.com
bright developers - A blog about software development, personal development, and personal finance
A blog about software development, personal development, and personal finance


 Miloserdov.org
Miloserdov.org
Ethical hacking and penetration testing - InfoSec, IT, Kali Linux, BlackArch
The complete guide to Wine: from installation to advanced usage Table of contents 1. Why Wine 2. Features and limitations of Wine 3. 64-bit or 32-bit Wine? 4. How to install Wine 4.1 Installing Wine on Debian, Kali Linux, Linux Mint, Ubuntu, and their derivatives 4.2 Installing Wine on Arch Linux 5. How...
 Decompiler.com
Decompiler.com
Java decompiler online / APK decompiler - Decompiler.com
Online decompiler for Java, Android, Python and C#.

 Cyberpunk.rs
Cyberpunk.rs
CYBERPUNK | The Best Tutorials & CyberSecurity Tool Reviews
CyberPunk: The Best Tutorials & CyberSecurity Tool Reviews. Get informed about the latest ethical hacking and cybersecurity tool releases. Read Cyberpunk's ethical hacking tutorials/articles and watch usage videos...
 Rootsh3ll.com
Rootsh3ll.com
welcome to rootsh3ll
Learn Penetration Testing by practice... A massive brute-force attack hit our application server in mid-2018, with around 500,000 login attempts at peak in just one day. That's massive, and we wouldn't have survived if we didn't have the necessary security implementations in the system beforehand. Simply put, we hacked our...

 Kalitutorials.net
Kalitutorials.net
Kali Linux Hacking Tutorials
Thursday, December 6, 2018 Bypassing website blocking/censorship with Secure DNS and Encrypted SNI (cloudflare only) By Shashwat December 06, 2018 blocking, bypassing, censorship, cloudflare, esni, firefox, nightly, tls, tls1.3 Disclaimer - TLDR; some stuff here can be used to carry out illegal activity, our intention is, however, to educate I...
 Decompileandroid.com
Decompileandroid.com
Android APK Decompiler
Decompiling APK files made easy Choose an APK file and upload it and we'll decompile it in just a couple minutes. Having trouble with the uploader? Try the static version instead. File: To see the progress of your upload try our new flash uploader. What does this do? All...

 Androiddecompiler.com
Androiddecompiler.com
AndroChef Java Decompiler
AndroChef Java Decompiler is Windows decompiler for class, jar, apk and dex files. It reconstructs the original source code from the compiled binary CLASS files (for example Java applets). AndroChef Java Decompiler is able to decompile the most complex Java 6 binaries, producing accurate source code.


 Vaibhavpandey.com
Vaibhavpandey.com
Vaibhav Pandey -aka- VPZ
vaibhavpandeyvpz's homepage for open-source web, mobile & native projects hosted at github.
 Kalitut.com
Kalitut.com
KaliTut Linux and pentesting blog - KaliTut
Windows PowerShell tutorial for beginners Detailed PowerShell tutorial for beginners! ✓ Create and run PowerShell script, practice-oriented knowledge about PowerShell. Learn to Hack Steps from Beginner to Hacker Learn to hack , Beginner's Guide - with some many Tutorials on how to Hack Computers with Kali Install Linux PowerShell Tutorial...

 Kali.tools
Kali.tools
Инструменты Kali Linux - Список инструментов для тестирования на проникновение и их описание
Сбор информации acccheck ace-voip Amap AQUATONE arp-scan Automater badKarma bing-ip2hosts braa Bro Bypass firewalls by abusing DNS history CaseFile CATPHISH CDPSnarf cisco-torch CloudFail Cookie Cadger copy-router-config DMitry dnmap dnsenum dnsmap DNSRecon dnstracer dnstwist dnswalk DotDotPwn Dublin Traceroute enum4linux enumIAX exploitdb EyeWitness Faraday FinalRecon Fierce Firewalk flashlight fragroute fragrouter Ghost Phisher...
Technologies Used by evilsocket.net
Dns Records of evilsocket.net
A Record: 172.67.178.148 104.21.35.183AAAA Record: 2606:4700:3037::ac43:b294 2606:4700:3031::6815:23b7
CNAME Record:
NS Record: sue.ns.cloudflare.com ben.ns.cloudflare.com
SOA Record: dns.cloudflare.com
MX Record: mail.protonmail.ch
SRV Record:
TXT Record: protonmail-verification=602a9d52eea7a6ebffa38be10065e106aa574889 keybase-site-verification=KGqS5gTVGpIu4qCBJFnsiexH59GN5jko7sjjlUFQogE v=spf1 include:_spf.protonmail.ch mx ~all google-site-verification=6qdVG0z0lac2ceITCoTCNm15CPp3K9Sq41_5IK4OLKM
DNSKEY Record:
CAA Record:
Whois Detail of evilsocket.net
Domain Name: EVILSOCKET.NETRegistry Domain ID: 1224985449_DOMAIN_NET-VRSN
Registrar WHOIS Server: whois.wildwestdomains.com
Registrar URL: https://www.wildwestdomains.com
Updated Date: 2018-06-20T08:20:52Z
Creation Date: 2007-09-18T18:06:07Z
Registrar Registration Expiration Date: 2023-09-18T18:06:07Z
Registrar: Wild West Domains, LLC
Registrar IANA ID: 440
Registrar Abuse Contact Email: [email protected]
Registrar Abuse Contact Phone: +1.4806242505
Reseller: Domains Priced Right
Domain Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited
Domain Status: clientUpdateProhibited https://icann.org/epp#clientUpdateProhibited
Domain Status: clientRenewProhibited https://icann.org/epp#clientRenewProhibited
Domain Status: clientDeleteProhibited https://icann.org/epp#clientDeleteProhibited
Registrant Organization:
Registrant State/Province: Rome
Registrant Country: IT
Registrant Email: Select Contact Domain Holder link at https://www.secureserver.net/whois?plid=1387&domain=EVILSOCKET.NET
Admin Email: Select Contact Domain Holder link at https://www.secureserver.net/whois?plid=1387&domain=EVILSOCKET.NET
Tech Email: Select Contact Domain Holder link at https://www.secureserver.net/whois?plid=1387&domain=EVILSOCKET.NET
Name Server: BEN.NS.CLOUDFLARE.COM
Name Server: SUE.NS.CLOUDFLARE.COM
DNSSEC: unsigned
URL of the ICANN WHOIS Data Problem Reporting System: http://wdprs.internic.net/
>>> Last update of WHOIS database: 2022-07-12T01:09:51Z <<<
For more information on Whois status codes, please visit https://icann.org/epp
TERMS OF USE: The data contained in this registrar's Whois database, while believed by the
registrar to be reliable, is provided "as is" with no guarantee or warranties regarding its
accuracy. This information is provided for the sole purpose of assisting you in obtaining
information about domain name registration records. Any use of this data for any other purpose
is expressly forbidden without the prior written permission of this registrar. By submitting
an inquiry, you agree to these terms and limitations of warranty. In particular, you agree not
to use this data to allow, enable, or otherwise support the dissemination or collection of this
data, in part or in its entirety, for any purpose, such as transmission by e-mail, telephone,
postal mail, facsimile or other means of mass unsolicited, commercial advertising or solicitations
of any kind, including spam. You further agree not to use this data to enable high volume, automated
or robotic electronic processes designed to collect or compile this data for any purpose, including
mining this data for your own personal or commercial purposes. Failure to comply with these terms
may result in termination of access to the Whois database. These terms may be subject to modification
at any time without notice.
 172.67.137.197
172.67.137.197
 United States
United States
 Valid SSL
Valid SSL