Information Security News|Cyber Security|Hacking Tutorial
Information Security Newspaper covers cyber security news, data breaches, malware, hacking, vulnerabilities, mobile security & ethical hacking tutorials

Stats
Alexa Rank:
Popular in Country:
Country Alexa Rank:
language: en-US
Response Time: 3.112057
SSL: Enable
Status: up
Code To Txt Ratio
Word Count 1817
Links
ratio 9.5602782564299
SSL Details
SSL Issuer:
Issuer: R3
Valid From: 2022-04-30 07:00:08
Expiration Date: 2022-07-29 07:00:07
SSL Organization:
Signature c47a21a65f183267ddbde5ad2f43b764ff0e843d
Algorithm: RSA-SHA256
Found 71 Top Alternative to Securitynewspaper.com


 Kalilinuxtutorials.com
Kalilinuxtutorials.com
Kali Linux Tutorials - A Single Stop for Kali Linux Tools
Kali Linux tutorials is an independent platform that covers step by tutorials, advanced penetration testing, Ethical Hacking and network security tools.

 Hackingloops.com
Hackingloops.com
Learn Ethical Hacking and Penetration Testing Online | Learn ethical hacking, penetration testing, cyber security, best security and web penetration testing techniques from best ethical hackers in security field.
Learn ethical hacking, penetration testing, cyber security, best security and web penetration testing techniques from best ethical hackers in security field.

 Kalilinux.in
Kalilinux.in
Best Kali Linux Tutorials
Best Place for Kali Linux Tutorials. Large number of articles on Kali Linux in easy steps from basic to advanced. Command by command with screenshots.
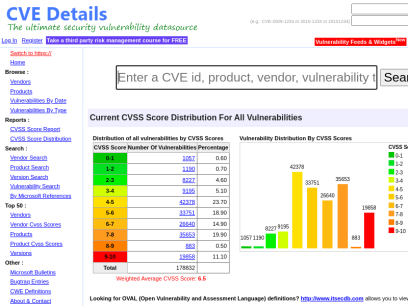
 Cvedetails.com
Cvedetails.com
CVE security vulnerability database. Security vulnerabilities, exploits, references and more
CVEdetails.com is a free CVE security vulnerability database/information source. You can view CVE vulnerability details, exploits, references, metasploit modules, full list of vulnerable products and cvss score reports and vulnerability trends over time

 Rapid7.com
Rapid7.com
Cybersecurity & Compliance Solutions & Services | Rapid7
Supercharge your security impact with Rapid7, delivering shared visibility, analytics, and automation to unite security, IT, and DevOps teams.

 Kitploit.com
Kitploit.com
KitPloit - PenTest & Hacking Tools
Leading source of security tools, hacking tools, cybersecurity and network security. Learn about new tools and updates in one place.

 Latesthackingnews.com
Latesthackingnews.com
Latest Hacking News - We offer the latest hacking news and cyber security courses for ethical hackers, penetration testers, IT security experts and essentially anyone with hacker interests.
We offer the latest hacking news and cyber security courses for ethical hackers, penetration testers, IT security experts and essentially anyone with hacker interests.

 Portswigger.net
Portswigger.net
Web Application Security, Testing, & Scanning - PortSwigger
PortSwigger offers tools for web application security, testing, & scanning. Choose from a range of security tools, & identify the very latest vulnerabilities.
 Wonderhowto.com
Wonderhowto.com
Wonder How To » Fresh Hacks For a Changing World
Wonder How To is your guide to free how to videos on the Web. Search, Browse and Discover the best how to videos across the web using the largest how to video index on the web. Watch the best online video instructions, tutorials, & How-Tos for free. Have your own how to videos? Submit them to share with the world.
 Nmap.org
Nmap.org
Nmap: the Network Mapper - Free Security Scanner
Nmap Free Security Scanner, Port Scanner, & Network Exploration Tool. Download open source software for Linux, Windows, UNIX, FreeBSD, etc.

 Miloserdov.org
Miloserdov.org
Ethical hacking and penetration testing - InfoSec, IT, Kali Linux, BlackArch
The complete guide to Wine: from installation to advanced usage Table of contents 1. Why Wine 2. Features and limitations of Wine 3. 64-bit or 32-bit Wine? 4. How to install Wine 4.1 Installing Wine on Debian, Kali Linux, Linux Mint, Ubuntu, and their derivatives 4.2 Installing Wine on Arch Linux 5. How...

 Pentesttools.net
Pentesttools.net
PentestTools - Penetration Testing Tools.
Latest Penetration Testing Tools. Cyber Security and Technology News. High Quality Penetration Testing Videos.
 Hackingblogs.com
Hackingblogs.com
Hacking Blogs - Latest Cyber Hacking News & Analysis
Become hacking blogs, Get latest hacking news, updates, security & patch news, all about ethical hacking, world most favorite blog for hacker community.

 Conzu.de
Conzu.de
conzu.de - This website is for sale! - conzu Resources and Information.
This website is for sale! conzu.de is your first and best source for all of the information you’re looking for. From general topics to more of what you would expect to find here, conzu.de has it all. We hope you find what you are searching for!
 Darknet.org.uk
Darknet.org.uk
Darknet - Hacking Tools, Hacker News & Cyber Security
Darknet is your best source for the latest hacking tools, hacker news, cyber security best practices, ethical hacking & pen-testing.

 Kali.tools
Kali.tools
Инструменты Kali Linux - Список инструментов для тестирования на проникновение и их описание
Сбор информации acccheck ace-voip Amap AQUATONE arp-scan Automater badKarma bing-ip2hosts braa Bro Bypass firewalls by abusing DNS history CaseFile CATPHISH CDPSnarf cisco-torch CloudFail Cookie Cadger copy-router-config DMitry dnmap dnsenum dnsmap DNSRecon dnstracer dnstwist dnswalk DotDotPwn Dublin Traceroute enum4linux enumIAX exploitdb EyeWitness Faraday FinalRecon Fierce Firewalk flashlight fragroute fragrouter Ghost Phisher...

 Hakin9.org
Hakin9.org
Home - Hakin9 - IT Security Magazine
Our tutorials, case studies and online courses will prepare you for the upcoming, potential threats in the cyber security world.

 Securityaffairs.co
Securityaffairs.co
Security Affairs - Read, think, share … Security is everyone's responsibilitySecurity Affairs
Security Affairs - Every security issue is our affair. Read, think, share … Security is everyone's responsibility
 Hackersonlineclub.com
Hackersonlineclub.com
Homepage - HackersOnlineClub
HackersOnlineClub is leading Cyber Security Tutorial Website. Learn Penetration Testing, Bug Bounty Tips, and Infosec Courses.
 Prodefence.org
Prodefence.org
Prodefence - Cyber Security Services | Malware & Pentesting
Cyber security services - Malware analysis - Penetration testing - Data protection
 Securityonline.info
Securityonline.info
Penetration Testing • Information Security
Securityonline is a huge security community. It is committed to the sharing of high-quality technical articles and safety reports, focusing on high-quality security and security incidents in the industry.
 Techtrick.in
Techtrick.in
Ethical Hacking,Kali Linux,WhatsApp Tricks,Hacking|TechTrick
Best site to get all working Whatsapp Tricks,Facebook Tricks,Kali Linux,Hacking Material,Ethical Hacking,TechTrick,Tech Trick,Techtricks,Akash Chugh for free.

 Yeahhub.com
Yeahhub.com
Yeah Hub - Kali Linux Tutorials | Tech News | SEO Tips and Tricks
Kali Linux Tutorials | Tech News | SEO Tips and Tricks

 Thehacktoday.com
Thehacktoday.com
Hack Today | Hacking News Platform that covers on Cyber Security, Privacy, Surveillance and Cyber Crime.
Hack Today is a News Platform that centers on InfoSec, Cyber Crime, Privacy, Surveillance and Hacking News with full-scale reviews on Social Media Platforms & Technology trends.

 Hackingvision.com
Hackingvision.com
HackingVision – Ethical Hacking Tutorials, Tips & Tricks, Kali Linux, Beginners Hacking
Top Colleges for Cybersecurity Degree Programs 1st June 2022 by Carl Hill Cybersecurity has a great job market with many job vacancies and attractive salaries. When you have a cybersecurity degree, you can easily find job opportunities such as security engineers. Therefore, training begins at the college level when you...
 Pentestlab.blog
Pentestlab.blog
Penetration Testing Lab – Offensive Techniques & Methodologies
Offensive Techniques & Methodologies


 0x00sec.org
0x00sec.org
0x00sec - The Home of the Hacker
The Home of the Hacker - Malware, Reverse Engineering, and Computer Science.

 Adminbooster.com
Adminbooster.com
Admin Booster - Salesforce.com administration
Salesforce administration through the command line.

 Kalitutorials.net
Kalitutorials.net
Kali Linux Hacking Tutorials
Thursday, December 6, 2018 Bypassing website blocking/censorship with Secure DNS and Encrypted SNI (cloudflare only) By Shashwat December 06, 2018 blocking, bypassing, censorship, cloudflare, esni, firefox, nightly, tls, tls1.3 Disclaimer - TLDR; some stuff here can be used to carry out illegal activity, our intention is, however, to educate I...
 Hackertarget.com
Hackertarget.com
28 Online Vulnerability Scanners & Network Tools | HackerTarget.com
Online Vulnerability Scanners to map the attack surface and identify vulnerabilities. 28 trusted open source security scanners and network tools.

 Kali.org
Kali.org
Kali Linux | Penetration Testing and Ethical Hacking Linux Distribution
Home of Kali Linux, an Advanced Penetration Testing Linux distribution used for Penetration Testing, Ethical Hacking and network security assessments.
 Hackread.com
Hackread.com
HackRead | Latest Cyber Crime - InfoSec- Tech - Hacking News
(adsbygoogle = window.adsbygoogle || ).push({});
 Hacking-tutorial.com
Hacking-tutorial.com
Ethical Hacking Tutorials, Tips and Tricks - Free Tutorials, Tools, How to's
Ethical Hacking Tutorial, Tips and Trick. Free hacking knowledge, learn how to hack
 Lewiscomputerhowto.blogspot.com
Lewiscomputerhowto.blogspot.com
Kali Linux Howto's
Complete tutorials on how to use Kali Linux and its tools.

 Aircrack-ng.org
Aircrack-ng.org
Aircrack-ng
Fresh news Aircrack-ng 1.7 10 May 22 After more than 2 years, we are making a release with a decently large amount of fixes, improvements, and additions. We also broke the 4000 commits barrier, and this release has more than 400 commits. Read more in our detailed blog post. PackageCloud.io...
 Concise-courses.com
Concise-courses.com
Resource For Hacker Tools & Growth / SEO Hacking Tools
Site Dedicated To Intrepid SEO Explorers

 1337pwn.com
1337pwn.com
1337pwn ⋆
1337pwn provides tutorials on ethical hacking, digital forensics, Kali Linux, Metasploit, WiFi hacking, and FTK Imager.

 Pentester.land
Pentester.land
Pentester Land · Offensive Infosec
The newsletter is dead, long live the newsletter! 12 Jul 2020 • newsletter This is a long due post. Since The 5 Hacking Newsletter has stopped on this blog, I’ve been getting many questions about it. So, even though most readers already know by now, here’s a summary of what...


 Cybersecurity-help.cz
Cybersecurity-help.cz
Vulnerability Intelligence by CyberSecurity Help s.r.o.
Actionable vulnerability intelligence for every company.

 Dnsdumpster.com
Dnsdumpster.com
DNSdumpster.com - dns recon and research, find and lookup dns records
Find dns records in order to identify the Internet footprint of an organization. Recon that enables deeper security assessments and discovery of the attack surface.

 Cyware.com
Cyware.com
Threat Intelligence Solution Company | Cyber Security Products | Cyber Security Operations Center | Cyware
Cyber Security Products - Cyware offers innovative, real-time cyber fusion solutions for Strategic and Tactical Threat Intelligence Sharing, Threat Response and Security Automation. Get a Demo Now!

 Thezerohack.com
Thezerohack.com
Home - The Zero Hack
Hacks / Security How I Found A Vulnerability To Hack iCloud Accounts and How Apple Reacted To It Laxman Muthiyah - June 20, 2021 19 This article is about how I found a vulnerability on Apple forgot password endpoint that allowed me to takeover an iCloud account. The vulnerability... Read...

 Cyberpunk.rs
Cyberpunk.rs
CYBERPUNK | The Best Tutorials & CyberSecurity Tool Reviews
CyberPunk: The Best Tutorials & CyberSecurity Tool Reviews. Get informed about the latest ethical hacking and cybersecurity tool releases. Read Cyberpunk's ethical hacking tutorials/articles and watch usage videos...
 Hsploit.com
Hsploit.com
HackerSploit Blog - Cybersecurity Training & Penetration Testing
HackerSploit is the leading provider of free Infosec and cybersecurity training. Our goal is to make cybersecurity training more effective and accessible to students and professionals. We achieve this by providing essential training on how to attack and defend systems with virtual labs and real-world scenarios. We offer individual and corporate training packages in Penetration Testing & Red Team Operations, Web application penetration testing, and cybersecurity awareness training.
 Opentechinfo.com
Opentechinfo.com
Opentech Info - Tech Tips & Tricks
The opentechinfo blog is a tech blog. Where you can find tutorial and knowledge related to android, hacking. My blog is basically a go-to guide about these topics.


 Blackarch.org
Blackarch.org
BlackArch Linux - Penetration Testing Distribution
BlackArch Linux is a lightweight expansion to Arch Linux for penetration testers.
 Hacking.land
Hacking.land
Hacking Land - Hack, Crack and Pentest
¿Recuerdan cuándo todo se hackeaba con Telnet y una IP? Pues bueno, hoy no...

 Hackingpassion.com
Hackingpassion.com
HackingPassion.com : [email protected][~]
HackingPassion.com Learn Ethical Hacking and Cyber-Security. We help people become ethical hackers so they can test security systems. We ♥ open-source and Linux

 Cyberpratibha.com
Cyberpratibha.com
Cyber Pratibha | Enhance Cyber Skills
One Step Towards, Secure Cyber Word It's your turn to help to secure cyber space by enhancing your technical skills including Expertise in Linux, Wireless Security, Advanced in Kali Linux, Ethical Hacking and more Start Your Journy Work as volunteer Online Classes One to one, One to many classes make you | Cyber Pratibha
 Securityequifax2017.com
Securityequifax2017.com
SecurityEquifax | CyberSecurity & Ethical Hacking Tutorials
Learn how to hack various online passwords in aim to recover your lost or hacked accounts. Monitor PC or mobile phone to supervise your children, and much more!
 Hacking.reviews
Hacking.reviews
Hacking Reviews
Leading source of Hacking News, Information Security, Cyber Security, and Network Security.
Technologies Used by securitynewspaper.com
Dns Records of securitynewspaper.com
A Record: 173.255.249.236AAAA Record:
CNAME Record:
NS Record: ns45.domaincontrol.com ns46.domaincontrol.com
SOA Record: dns.jomax.net
MX Record: mx.zoho.com mx3.zoho.com mx2.zoho.com
SRV Record:
TXT Record: zoho-verification=zb15611119.zmverify.zoho.com v=spf1 include:zoho.com ~all
DNSKEY Record:
CAA Record:
Whois Detail of securitynewspaper.com
Domain Name: SECURITYNEWSPAPER.COMRegistry Domain ID: 1955170286_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.godaddy.com
Registrar URL: https://www.godaddy.com
Updated Date: 2020-04-15T02:49:25Z
Creation Date: 2015-08-25T03:13:59Z
Registrar Registration Expiration Date: 2025-08-25T03:13:59Z
Registrar: GoDaddy.com, LLC
Registrar IANA ID: 146
Registrar Abuse Contact Email: [email protected]
Registrar Abuse Contact Phone: +1.4806242505
Domain Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited
Domain Status: clientUpdateProhibited https://icann.org/epp#clientUpdateProhibited
Domain Status: clientRenewProhibited https://icann.org/epp#clientRenewProhibited
Domain Status: clientDeleteProhibited https://icann.org/epp#clientDeleteProhibited
Registry Registrant ID: Not Available From Registry
Registrant Name: Registration Private
Registrant Organization: Domains By Proxy, LLC
Registrant Street: DomainsByProxy.com
Registrant Street: 2155 E Warner Rd
Registrant City: Tempe
Registrant State/Province: Arizona
Registrant Postal Code: 85284
Registrant Country: US
Registrant Phone: +1.4806242599
Registrant Phone Ext:
Registrant Fax: +1.4806242598
Registrant Fax Ext:
Registrant Email: Select Contact Domain Holder link at https://www.godaddy.com/whois/results.aspx?domain=SECURITYNEWSPAPER.COM
Registry Admin ID: Not Available From Registry
Admin Name: Registration Private
Admin Organization: Domains By Proxy, LLC
Admin Street: DomainsByProxy.com
Admin Street: 2155 E Warner Rd
Admin City: Tempe
Admin State/Province: Arizona
Admin Postal Code: 85284
Admin Country: US
Admin Phone: +1.4806242599
Admin Phone Ext:
Admin Fax: +1.4806242598
Admin Fax Ext:
Admin Email: Select Contact Domain Holder link at https://www.godaddy.com/whois/results.aspx?domain=SECURITYNEWSPAPER.COM
Registry Tech ID: Not Available From Registry
Tech Name: Registration Private
Tech Organization: Domains By Proxy, LLC
Tech Street: DomainsByProxy.com
Tech Street: 2155 E Warner Rd
Tech City: Tempe
Tech State/Province: Arizona
Tech Postal Code: 85284
Tech Country: US
Tech Phone: +1.4806242599
Tech Phone Ext:
Tech Fax: +1.4806242598
Tech Fax Ext:
Tech Email: Select Contact Domain Holder link at https://www.godaddy.com/whois/results.aspx?domain=SECURITYNEWSPAPER.COM
Name Server: NS45.DOMAINCONTROL.COM
Name Server: NS46.DOMAINCONTROL.COM
DNSSEC: unsigned
URL of the ICANN WHOIS Data Problem Reporting System: http://wdprs.internic.net/
>>> Last update of WHOIS database: 2022-06-20T18:22:55Z <<<
For more information on Whois status codes, please visit https://icann.org/epp
TERMS OF USE: The data contained in this registrar's Whois database, while believed by the
registrar to be reliable, is provided "as is" with no guarantee or warranties regarding its
accuracy. This information is provided for the sole purpose of assisting you in obtaining
information about domain name registration records. Any use of this data for any other purpose
is expressly forbidden without the prior written permission of this registrar. By submitting
an inquiry, you agree to these terms and limitations of warranty. In particular, you agree not
to use this data to allow, enable, or otherwise support the dissemination or collection of this
data, in part or in its entirety, for any purpose, such as transmission by e-mail, telephone,
postal mail, facsimile or other means of mass unsolicited, commercial advertising or solicitations
of any kind, including spam. You further agree not to use this data to enable high volume, automated
or robotic electronic processes designed to collect or compile this data for any purpose, including
mining this data for your own personal or commercial purposes. Failure to comply with these terms
may result in termination of access to the Whois database. These terms may be subject to modification
at any time without notice.
 104.18.12.238
104.18.12.238
 United States
United States
 Valid SSL
Valid SSL