Hacking Articles - Raj Chandel's Blog
Raj Chandel's Blog

Stats
Alexa Rank:
Popular in Country:
Country Alexa Rank:
language: en
Response Time: 1.330071
SSL: Enable
Status: up
Code To Txt Ratio
Word Count 894
Links
ratio 12.614993777185
SSL Details
SSL Issuer:
Issuer: Cloudflare Inc ECC CA-3
Valid From: 2022-01-08 00:00:00
Expiration Date: 2023-01-07 23:59:59
SSL Organization:
Signature ab36262cbdb3af306d1876f5e230cde291bbfd34
Algorithm: ecdsa-with-SHA256
Found 75 Top Alternative to Hackingarticles.in
 Pentestlab.blog
Pentestlab.blog
Penetration Testing Lab – Offensive Techniques & Methodologies
Offensive Techniques & Methodologies

 Kalilinuxtutorials.com
Kalilinuxtutorials.com
Kali Linux Tutorials - A Single Stop for Kali Linux Tools
Kali Linux tutorials is an independent platform that covers step by tutorials, advanced penetration testing, Ethical Hacking and network security tools.

 Vulnhub.com
Vulnhub.com
Vulnerable By Design ~ VulnHub
VulnHub provides materials allowing anyone to gain practical hands-on experience with digital security, computer applications and network administration tasks.
 Hackthebox.eu
Hackthebox.eu
Hack The Box: Hacking Training For The Best | Individuals & Companies
Where hackers level up! An online cybersecurity training platform allowing IT professionals to advance their ethical hacking skills and be part of a worldwide community. Join today and learn how to hack!
 Elearnsecurity.com
Elearnsecurity.com
Cyber Security Certifications - eLearnSecurity - eLearnSecurity
Trusted by HR departments around the world, our certifications are scenario-based exams that prove your cyber security skills in the job market. Infosec careers are heating up and candidates are doing everything they can to stand out. Passing an eLearnSecurity certification shows potential employers that you have proven red, blue and purple team capabilities.

 Hacker101.com
Hacker101.com
Home | Hacker101
Hacker101 is a free class for web security. Whether you’re a programmer with an interest in bug bounties or a seasoned security professional, Hacker101 has something to teach you.
 Cvedetails.com
Cvedetails.com
CVE security vulnerability database. Security vulnerabilities, exploits, references and more
CVEdetails.com is a free CVE security vulnerability database/information source. You can view CVE vulnerability details, exploits, references, metasploit modules, full list of vulnerable products and cvss score reports and vulnerability trends over time

 Rapid7.com
Rapid7.com
Cybersecurity & Compliance Solutions & Services | Rapid7
Supercharge your security impact with Rapid7, delivering shared visibility, analytics, and automation to unite security, IT, and DevOps teams.
 Securityonline.info
Securityonline.info
Penetration Testing • Information Security
Securityonline is a huge security community. It is committed to the sharing of high-quality technical articles and safety reports, focusing on high-quality security and security incidents in the industry.
 Tryhackme.com
Tryhackme.com
TryHackMe | Cyber Security Training
TryHackMe is a free online platform for learning cyber security, using hands-on exercises and labs, all through your browser!
 Gtfobins.github.io
Gtfobins.github.io
GTFOBins
ab File upload File download SUID Sudo agetty SUID alpine File read SUID Sudo ansible-playbook Shell Sudo apt-get Shell Sudo apt Shell Sudo ar File read SUID Sudo aria2c Command Sudo Limited SUID arj File write File read SUID Sudo arp File read SUID Sudo as File read SUID Sudo...

 Cybersecurity-help.cz
Cybersecurity-help.cz
Vulnerability Intelligence by CyberSecurity Help s.r.o.
Actionable vulnerability intelligence for every company.

 Pentesterlab.com
Pentesterlab.com
PentesterLab: Learn Web Penetration Testing: The Right Way
WHAT OUR PRO MEMBERS SAY: 10010101 10110110 1010 “I consider PentesterLab to be a great resource for learning about web application security and ways how it can be subverted. Even though the exercises usually don’t take much time to complete they can teach a lot. I can’t but recommend it,...

 Packetstormsecurity.com
Packetstormsecurity.com
Packet Storm
Information Security Services, News, Files, Tools, Exploits, Advisories and Whitepapers

 Portswigger.net
Portswigger.net
Web Application Security, Testing, & Scanning - PortSwigger
PortSwigger offers tools for web application security, testing, & scanning. Choose from a range of security tools, & identify the very latest vulnerabilities.
 Nmap.org
Nmap.org
Nmap: the Network Mapper - Free Security Scanner
Nmap Free Security Scanner, Port Scanner, & Network Exploration Tool. Download open source software for Linux, Windows, UNIX, FreeBSD, etc.
 Bugcrowd.com
Bugcrowd.com
#1 Crowdsourced Cybersecurity Platform | Bugcrowd
Bugcrowd teams with elite security researchers to reduce risk & improve security ROI through our bug bounty, pen testing, & vulnerability disclosure programs.
 Securityidiots.com
Securityidiots.com
Welcome to Security Idiots!!
Security Idiots is a place where some insane idiots try thier hands on with Security.
 Crackstation.net
Crackstation.net
CrackStation - Online Password Hash Cracking - MD5, SHA1, Linux, Rainbow Tables, etc.
Crackstation is the most effective hash cracking service. We crack: MD5, SHA1, SHA2, WPA, and much more...

 Infosecinstitute.com
Infosecinstitute.com
IT & Security Education, Certifications, Awareness & Phishing Simulator - Infosec
Infosec helps IT and security professionals advance their careers with skills development and certifications while empowering all employees with security awareness and privacy training to stay cyber-safe at work and home.

 Netsparker.com
Netsparker.com
Invicti | Web Application Security For Enterprise
Get accurate, automated application security testing that scales like no other solution. Secure 1000s of web assets with less manual effort. Reduce your risk with the only…
 Ctftime.org
Ctftime.org
CTFtime.org / All about CTF (Capture The Flag)
Capture The Flag, CTF teams, CTF ratings, CTF archive, CTF writeups

 Asciinema.org
Asciinema.org
asciinema - Record and share your terminal sessions, the simple way
core/ca-certificates-utils 20210603-1 [instal.. │ Last Modified : Mon, 08 Ju core/coreutils 8.32-1 [installed] │ Out Of Date : No core/cracklib 2.9.7-2 [installed] │ core/crda 4.14-4 │ core/cronie 1.5.7-2 │ core/cryptsetup 2.4.0-1 [installed] │ core/curl 7.78.0-1 [installed] │ core/dash 0.5.11.4-1 │ core/db 5.3.28-5 [installed] │ core/dbus 1.12.20-1 [installed] │ core/dbus-docs 1.12.20-1...

 Mitre.org
Mitre.org
The MITRE Corporation
About Corporate Overview Our History Mission and Values Visiting MITRE Leadership Executive Team Board of Trustees Fellows Technical Fellows Visiting Fellows Awards and Recognition Corporate Social Responsibility Building a Foundation for the Future MITRE Staff Cultivates Los Angeles' Science Ecosystem Bringing Real World STEM to Students Building Partnerships and Diversity,...

 Root-me.org
Root-me.org
Bienvenue [Root Me : plateforme d'apprentissage dédiée au Hacking et à la Sécurité de l'Information]
Root Me est une plateforme permettant à chacun de tester et d'améliorer ses connaissances dans le domaine de la sécurité informatique et du hacking à travers la publication de challenges, de solutions, d'articles.
 Hackerone.com
Hackerone.com
HackerOne | #1 Trusted Security Platform and Hacker Program
Reduce your cybersecurity risk/vulnerabilities through bug bounty programs, VDPs, attack resistance management, attack surface management, security assessments, and pentest solutions.

 Kali.org
Kali.org
Kali Linux | Penetration Testing and Ethical Hacking Linux Distribution
Home of Kali Linux, an Advanced Penetration Testing Linux distribution used for Penetration Testing, Ethical Hacking and network security assessments.

 Sans.org
Sans.org
Cyber Security Training | SANS Courses, Certifications & Research
SANS Institute is the most trusted resource for cybersecurity training, certifications and research. Offering more than 60 courses across all practice areas, SANS trains over 40,000 cybersecurity professionals annually.

 Latesthackingnews.com
Latesthackingnews.com
Latest Hacking News - We offer the latest hacking news and cyber security courses for ethical hackers, penetration testers, IT security experts and essentially anyone with hacker interests.
We offer the latest hacking news and cyber security courses for ethical hackers, penetration testers, IT security experts and essentially anyone with hacker interests.

 Acunetix.com
Acunetix.com
Acunetix | Web Application Security Scanner
Acunetix is an end-to-end web security scanner that offers a 360 view of an organization’s security. Allowing you to take control of the security of all you web applications, web services, and APIs to ensure long-term protection. Acunetix’s scanning engine is globally known and trusted for its unbeatable speed and precision.
 Cxsecurity.com
Cxsecurity.com
CXSECURITY.COM Free Security List
CXSECURITY (Independent information about security) is a huge collection of information on data communications safety. Its main objective is to inform about errors in various applications.

 Bgasecurity.com
Bgasecurity.com
Ana Sayfa - BGA Security
Danışmanlık Hizmetleri Siber Güvenlik Danışmanlığı Teknolojinin gelişimi ile birlikte her geçen gün gelişen ve yenilenen siber saldırılara karşı şirketlere, kamu kuruluşlarına ve özel kurumlara siber güvenlik alanlarında ihtiyaç duydukları danışmanlık ve eğitim desteği sunuyoruz. Ürün bağımsız siber güvenlik yaklaşımımız sayesinde “güvenlik satan değil, güvenlik sağlayan” bir şirket olarak müşterilerimizin her...

 Pentester.land
Pentester.land
Pentester Land · Offensive Infosec
The newsletter is dead, long live the newsletter! 12 Jul 2020 • newsletter This is a long due post. Since The 5 Hacking Newsletter has stopped on this blog, I’ve been getting many questions about it. So, even though most readers already know by now, here’s a summary of what...

 Siberportal.org
Siberportal.org
SİBER GÜVENLİK PORTALİ | Bilgi güvenliği ve siber güvenlik, sızma testleri, güvenli sistem kurulumu ve yönetimi ile ilgili makalelerin yayınlandığı siber güvenlik portali…
Spanning Tree Protocol (IEEE 802.1D) 01/04/2022 0 Ethernet ağları, herhangi iki cihaz arasında tek bir yola sahip, döngüsüz bir topoloji gerektirir. Ancak kesintileri azaltmak ve erişilebilirliği iyileştirmek için yedekli yapılar kurulur.... Honeypot Sistemleri 19/03/2022 0 Honeypot bir saldırganın sistemlere yaptığı saldırıları, etkinlikleri tespit etmek için kullanılan kasıtlı olarak savunmasız bırakılan...
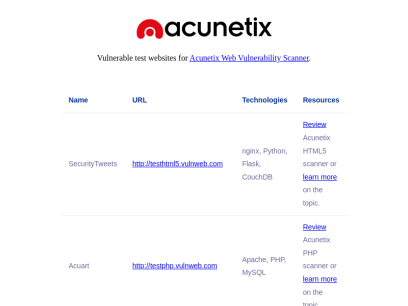
 Vulnweb.com
Vulnweb.com
Acunetix Web Vulnerability Scanner - Test websites
SecurityTweets http://testhtml5.vulnweb.com nginx, Python, Flask, CouchDB Review Acunetix HTML5 scanner or learn more on the topic. Acuart http://testphp.vulnweb.com Apache, PHP, MySQL Review Acunetix PHP scanner or learn more on the topic. Acuforum http://testasp.vulnweb.com IIS, ASP, Microsoft SQL Server Review Acunetix SQL scanner or learn more on the topic. Acublog http://testaspnet.vulnweb.com...

 Intigriti.com
Intigriti.com
Intigriti - Bug Bounty & Agile Pentesting Platform
Intigriti offers bug bounty and agile penetration testing solutions powered by Europe's #1 leading network of ethical hackers.
 Hackertarget.com
Hackertarget.com
28 Online Vulnerability Scanners & Network Tools | HackerTarget.com
Online Vulnerability Scanners to map the attack surface and identify vulnerabilities. 28 trusted open source security scanners and network tools.

 Detectify.com
Detectify.com
Attack Surface Management Tool Powered By Ethical Hackers | Detectify
Detectify's external attack surface management tool - assess, prioritize, remediate continuously growing external attack surfaces.


 Netsparker.com.tr
Netsparker.com.tr
Netsparker Türkiye - Web Uygulaması Güvenlik Tarayıcısı
Web siteleriniz ve web servislerinizdeki güvenlik açıklarını otomatik olarak tespit eden, false-positive (hatalı) bulgu raporlamayan, hızlı ve kullanımı kolay web uygulama güvenliği tarayıcıları.

 Hashcat.net
Hashcat.net
hashcat - advanced password recovery
World's fastest and most advanced password recovery utility

 Owasp.org
Owasp.org
OWASP Foundation | Open Source Foundation for Application Security
OWASP Foundation, the Open Source Foundation for Application Security on the main website for The OWASP Foundation. OWASP is a nonprofit foundation that works to improve the security of software.

 Blackhat.com
Blackhat.com
Black Hat | Home
Black Hat Webinars Security Research in Real Time June 30, 2022 - Managing Cybersecurity as a Business Risk July 14, 2022 - InfoSec Lessons from the War in Ukraine Sponsor a Webinars View all of our recent Webinars Black Hat Archives Watch Past Presentations View all of our archived videos...
 Wonderhowto.com
Wonderhowto.com
Wonder How To » Fresh Hacks For a Changing World
Wonder How To is your guide to free how to videos on the Web. Search, Browse and Discover the best how to videos across the web using the largest how to video index on the web. Watch the best online video instructions, tutorials, & How-Tos for free. Have your own how to videos? Submit them to share with the world.

 Cybrary.it
Cybrary.it
Free Cybersecurity Training and Career Development | Cybrary
Cybersecurity training from Cybrary will take your career to the next level. We have the cybersecurity courses that can help get you there!

 Tunnelsup.com
Tunnelsup.com
TunnelsUp - Tools and Information for Network Engineers
Tools, calculator, and helpful information for network engineering, web developers, and IT professionals.
 Tenable.com
Tenable.com
Tenable® - The Cyber Exposure Company
Welcome to the modern era of cyber exposure. Join the movement.

 Defcon.org
Defcon.org
DEF CON® Hacking Conference Home
The largest hacking and security conference with presentations, workshops, contests, villages and the premier Capture The Flag Contest.

 Parrotlinux.org
Parrotlinux.org
Parrot Security
ParrotSEC The operating system for | The ultimate framework for your Cyber Security operations Download Get Started What's new in ParrotOS 5.0 Electro Ara Tools for every operation Choose between 600+ tools for every kind of Red and Blue team operation. Parrot Security provides a huge arsenal of tools, utilities...

 Stationx.net
Stationx.net
StationX - The #1 Cyber Security Career Development Platform
Grow your skills and advance your career with StationX - the #1 Cyber Security Career Development Platform.

 Yeahhub.com
Yeahhub.com
Yeah Hub - Kali Linux Tutorials | Tech News | SEO Tips and Tricks
Kali Linux Tutorials | Tech News | SEO Tips and Tricks
 Darknet.org.uk
Darknet.org.uk
Darknet - Hacking Tools, Hacker News & Cyber Security
Darknet is your best source for the latest hacking tools, hacker news, cyber security best practices, ethical hacking & pen-testing.


 Miloserdov.org
Miloserdov.org
Ethical hacking and penetration testing - InfoSec, IT, Kali Linux, BlackArch
The complete guide to Wine: from installation to advanced usage Table of contents 1. Why Wine 2. Features and limitations of Wine 3. 64-bit or 32-bit Wine? 4. How to install Wine 4.1 Installing Wine on Debian, Kali Linux, Linux Mint, Ubuntu, and their derivatives 4.2 Installing Wine on Arch Linux 5. How...

 Securitynewspaper.com
Securitynewspaper.com
Information Security News|Cyber Security|Hacking Tutorial
Information Security Newspaper covers cyber security news, data breaches, malware, hacking, vulnerabilities, mobile security & ethical hacking tutorials
 Kitploit.com
Kitploit.com
KitPloit - PenTest & Hacking Tools
Leading source of security tools, hacking tools, cybersecurity and network security. Learn about new tools and updates in one place.
 Aldeid.com
Aldeid.com
aldeid
Pentesting   •    Web Exploitation   •    Cryptography   •    Forensics   •    Reversing   •    Binary Exploitation   •    CTF   •    Threat Hunting TryHackMe > Unbaked Pie Sun, 6 Jun 2021 11:34:00 +0000 Enumerate a Django application, find a vulnerability, exploit a pickle session cookie, evade a docker environment, find a way to forward ports, brute force an SSH account, this challenge...

 1337pwn.com
1337pwn.com
1337pwn ⋆
1337pwn provides tutorials on ethical hacking, digital forensics, Kali Linux, Metasploit, WiFi hacking, and FTK Imager.

 Pentestmonkey.net
Pentestmonkey.net
pentestmonkey | Taking the monkey work out of pentesting
mimikatz: Tool To Recover Cleartext Passwords From Lsass December 20, 2011, pentestmonkey I meant to blog about this a while ago, but never got round to it. Here’s a brief post about very cool feature of a tool called mimikatz. I’m very grateful to the tool’s author for bringing it...

 0x00sec.org
0x00sec.org
0x00sec - The Home of the Hacker
The Home of the Hacker - Malware, Reverse Engineering, and Computer Science.


 Hashes.com
Hashes.com
Decrypt MD5, SHA1, MySQL, NTLM, SHA256, SHA512, Wordpress, Bcrypt hashes for free online
Decrypt and crack your MD5, SHA1, SHA256, MySQL, and NTLM hashes for free online. We also support Bcrypt, SHA512, Wordpress and many more.

 Gracefulsecurity.com
Gracefulsecurity.com
Akimbo Core
Your Vulnerability Management Sucks Published: 16 March 2022 On March 16th I had the pleasure of speaking at the Yorkshire Cyber Security Cluster about Vulnerability Management. I've included my slides from the presentation and some speaker notes on the content covered here. Continue Reading HTTP Security Headers: Cache-Control Published: 21...
Technologies Used by hackingarticles.in
Dns Records of hackingarticles.in
A Record: 104.21.13.249 172.67.133.142AAAA Record: 2606:4700:3035::6815:df9 2606:4700:3031::ac43:858e
CNAME Record:
NS Record: duke.ns.cloudflare.com kay.ns.cloudflare.com
SOA Record: dns.cloudflare.com
MX Record: alt1.aspmx.l.google.com aspmx.l.google.com aspmx2.googlemail.com
SRV Record:
TXT Record: v=spf1 a mx ptr include:secureserver.net ~all
DNSKEY Record:
CAA Record:
 192.0.78.24
192.0.78.24
 United States
United States
 Valid SSL
Valid SSL